If you missed Part 1, you can check it out here. In Part 2, we’re going to talk about wallets–a software category that is the key to the whole decentralized identity ecosystem. In this blog we will consider the wallet as it pertains to identity infrastructure, including how a wallet does these things:
- Authenticate the person who is using it
- Store and present identity data
- Confirm the identity of the third party to which the wallet is sharing data (the “Verifier”)
- Cryptographically sign assertions presented to the Verifier
- Optionally support offline transactions
Broadly speaking, there are two types of wallets: custodial and non-custodial. A wallet is custodial if the private keys are stored in the cloud. The challenge of a non-custodial wallet is that if you lose access to the private key, anything contained in the wallet is lost. Consumers are well known for not backing up important data. This is a recipe for disaster, although technologists are working on ways to recover–for example by distributing key material to people you trust. Custodial wallets are problematic but convenient. For example, the third party that controls your custodial wallet could share your private key with authorities. Or the third party could prevent your access to the private key, essentially deplatforming you.
Despite our aspirations for the wallet as a piece of identity infrastructure, the three categories of wallets in use today are:
- Cryptocurrency Wallets
- Payment Wallets
- Mobile Driverslicense Wallets
I’m not a cryptocurrency expert, but I think most blockchains have a non-custodial wallet. Electrum is one of the oldest non-custodial wallets for Bitcoin. The most common non-custodial wallet for Ethereum-based blockchains is probably Metamask. Stych has released an interesting wallet called Vessel, which connects to both the Ethereum and Solana blockchains (and purports to hold identity credentials). People who are into cryptocurrency frequently conflate their wallet with their actual identity. Control of a wallet might be evidence of an identity (it’s a “something you have”, if you previously associated it with an account). One misconception of cryptocurrency wallets is that they “hold” funds. They do not–they simply protect the private key which proves ownership of assets that are recorded on a blockchain.
Apple, Google and Visa have payment wallets, which enable you to use NFC at a point of sales device to buy stuff. However, as mentioned in Part I of this blog series, the Apple Wallet is also trusted by several US states to hold a mobile Driverlicense (mDL). And the Apple Wallet is trusted by the US TSA to present the mDL for travel at several airports. So we are witnessing the convergence of payment and identity wallets. mDL is an ISO standard, and as such, interfaces for presentation have been mapped, including how to use Bluetooth in an offline scenario. And several vendors,like Idemia and GET Group, are creating standalone mDL applications that have interesting security properties.
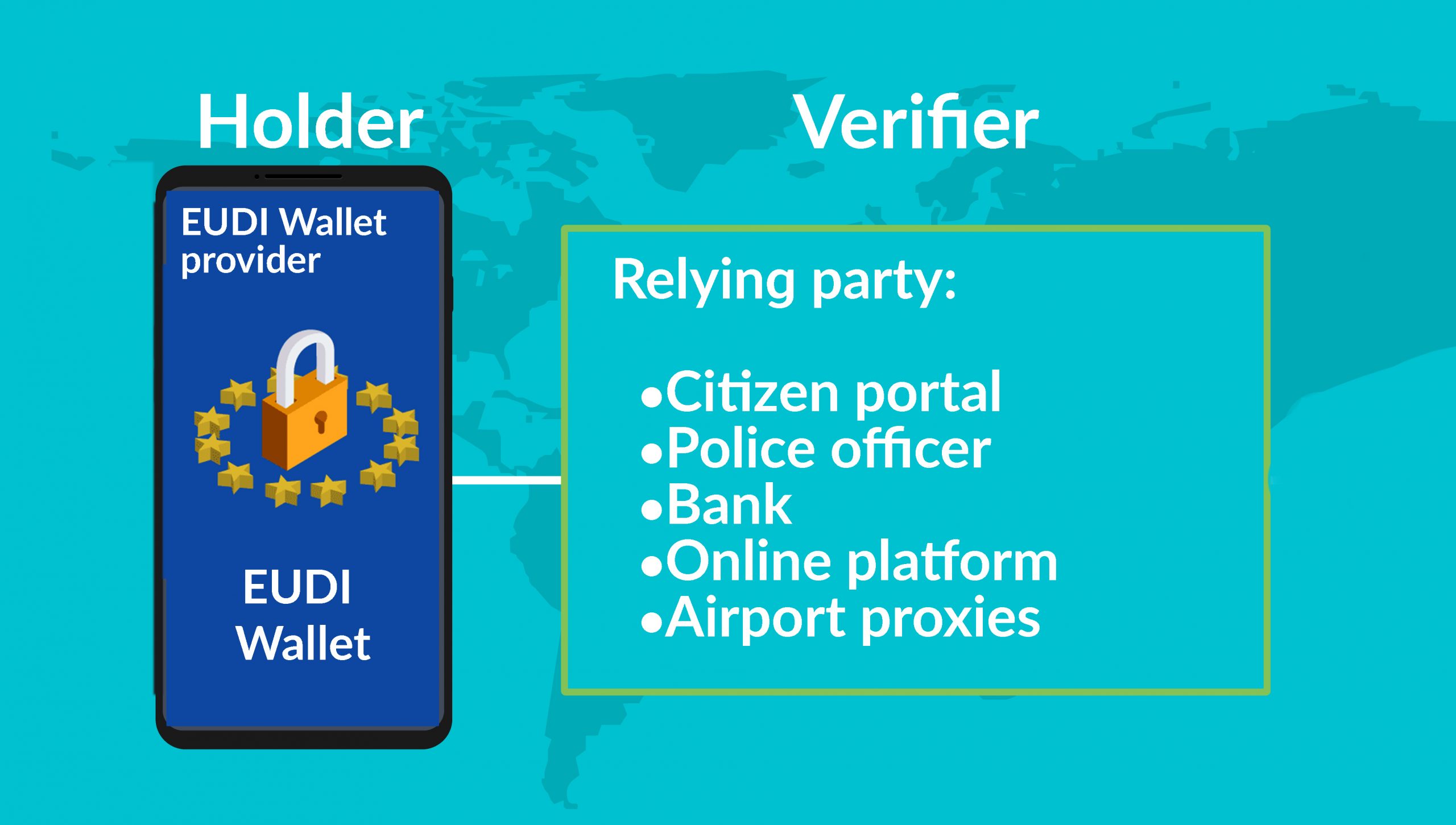
On of the most ambitious projects to create a wallet purpose-built for digital identity is the European Union Digital Identity Wallet Consortium (the “EUDI Wallet”). This is a requirement to fulfill the proposed eIDAS 2.0 legislation. If you don’t remember, eIDAS 1.0 envisions a big PKI solution, which many countries tried to implement using smart cards. A mobile wallet has the potential to be less expensive, easier to integrate, and better able to protect a person’s privacy. PKI is not going away, but it’s application could be more tactical and behind-the-scenes, lowering the deployment complexity. The EUDI Wallet is very early stage–basically drawing board, so don’t hold your breath just yet for it’s arrival.
In conclusion, while the wallet is a much talked about piece of software, it’s still early days. It’s exact role is not as well-defined as a web browser. Who will provide the wallet, what standards it will implement, the expected paradigms of user experience, key recovery, and many other details are not yet settled. And yet, without the standardization of the wallet functionality, decentralized identity will have to wait.