Self-Service MFA with Casa
A self-service credential management portal key to a successful MFA rollout. Casa provides this portal, enabling end users to register credentials: FIDO, TOTP, Super Gluu, SMS, X.509 Certificates, external IDPs. Casa plugins support additional third party authentication providers. Casa provides out-of-the-box MFA features for organizations that don’t need the flexibility of Agama to provide that extra level of customization.
MFA
Multi-Factor Authentication Under One Roof
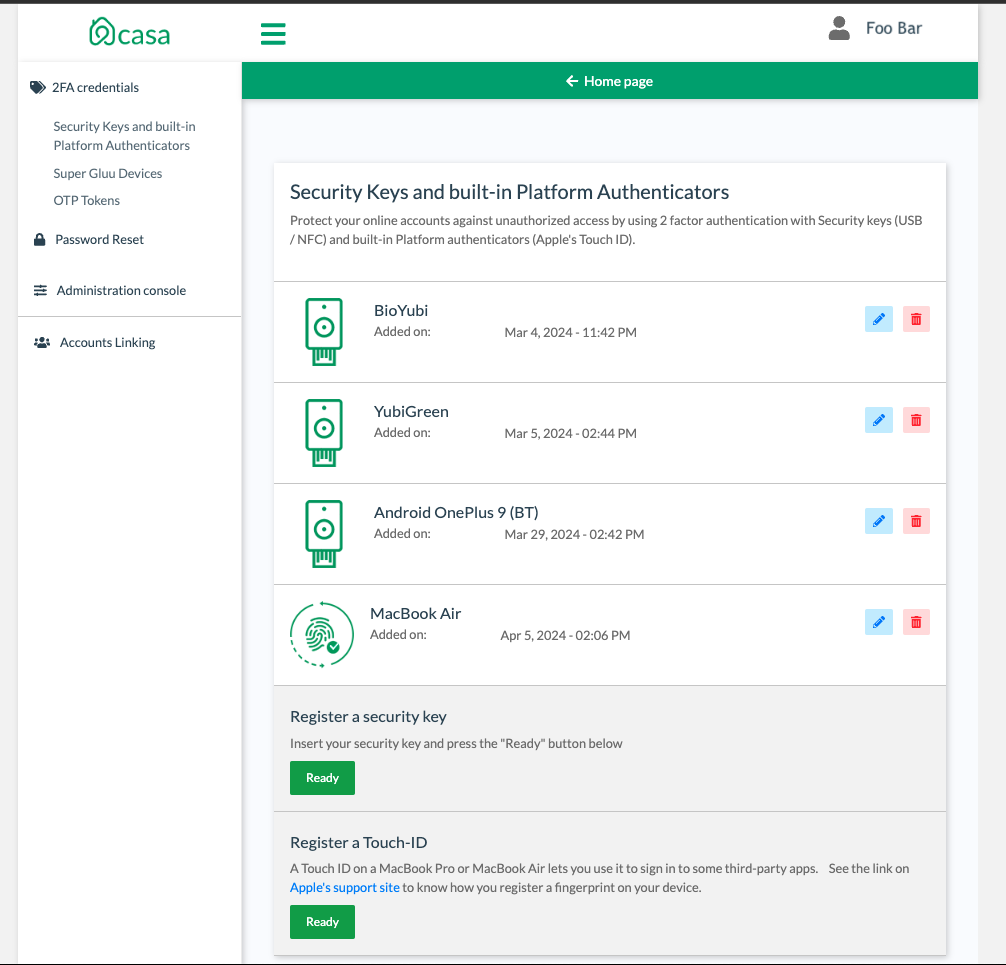
People have a lot of credentials. Casa provides a single point of management for end users to view, enroll, and remove MFA credentials, including FIDO passkeys, software tokens, biometric credentials, and external federated accounts (e.g. Google, Microsoft Entra, Apple). Casa is brandable and extensible. You can write plugins to support third party authentication services, or to perform identity mangement “light” features like registraiton approval or delegated administration.

Deploy cloud-native
If you love Kubernetes, or services like Amazon EKS, Google GKE or SUSE Rancher, then Casa is for you! Casa supports cloud native deployments using standards tools like Helm. Casa also supports multiple database backends, including LDAP, Couchbase, RDBMS, Amazon Aurora, and Google Spanner.
Enforce strong authentication
No more password resets
Self Service MFA done right
In the old days “password-reset” was a standard identity management (IDM) feature. Every IDM still has this capability today. But as organizations roll-out MFA, this “password-reset” process needs an upgrade. Technology leaders like Google or Gitlab enable end-users to see all their various MFA credentials on one page; end users can also add and remove new credentials. With Casa, your business can manage MFA like the pros!
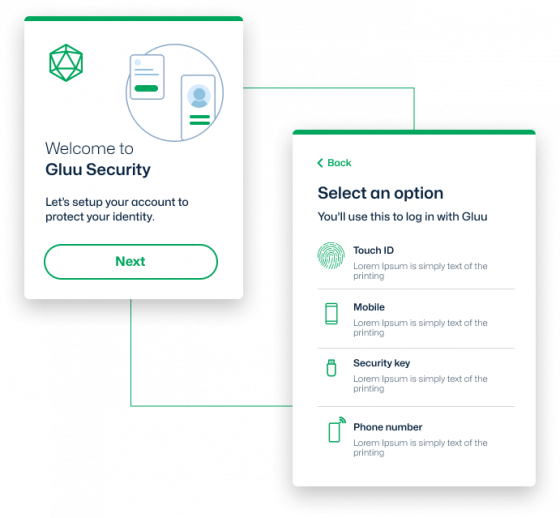
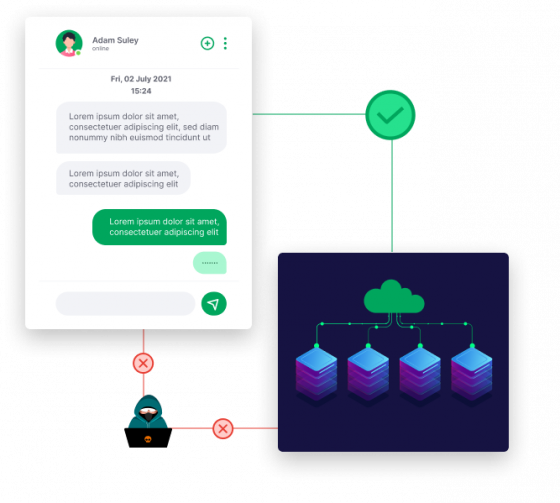
Eliminate Phishing with FIDO
To defeat phishing, we need to stop the “Man in the Middle” (MITM) attack. Passwords are vulnerable, but so are OTP tokens and mobile push notifications. In order to block phishing, we need end users to start using FIDO passkeys. The first step is to enable end-users to enroll USB, platform and Bluetooth FIDO credentials in your IDP. Let end users register as many devices as they want. Maybe you don’t even need to store toxic passwords?
Easy to use the credentials people have
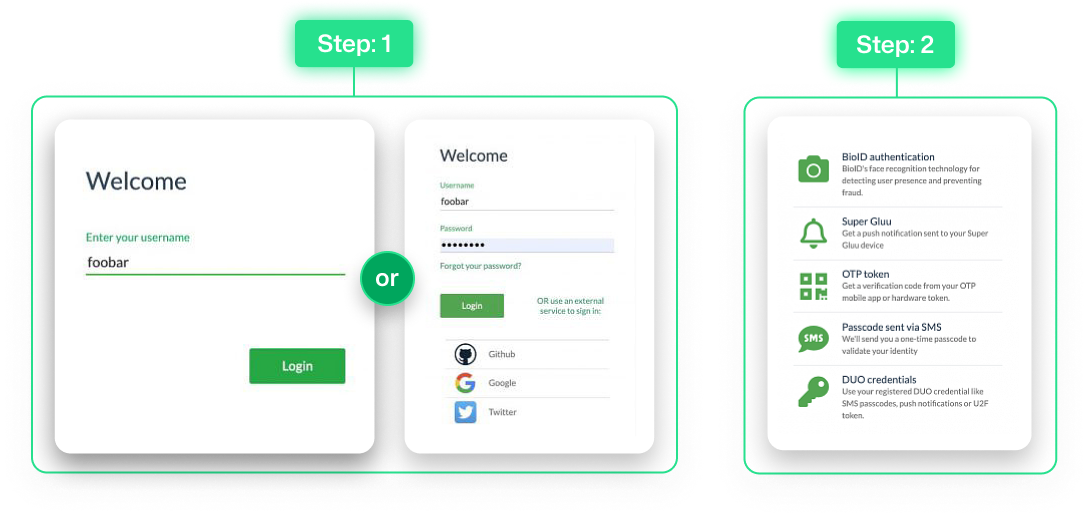
What is Lorem
Multi-Factor Authentication Under One Roof
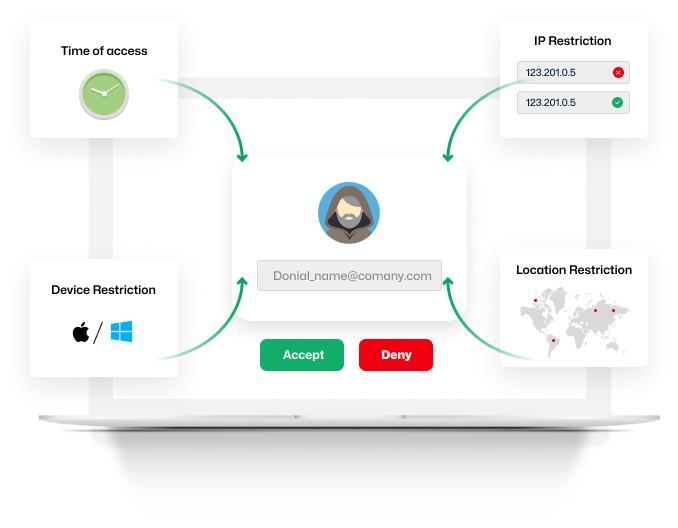
Adaptive Authentication
Location-based Authentication
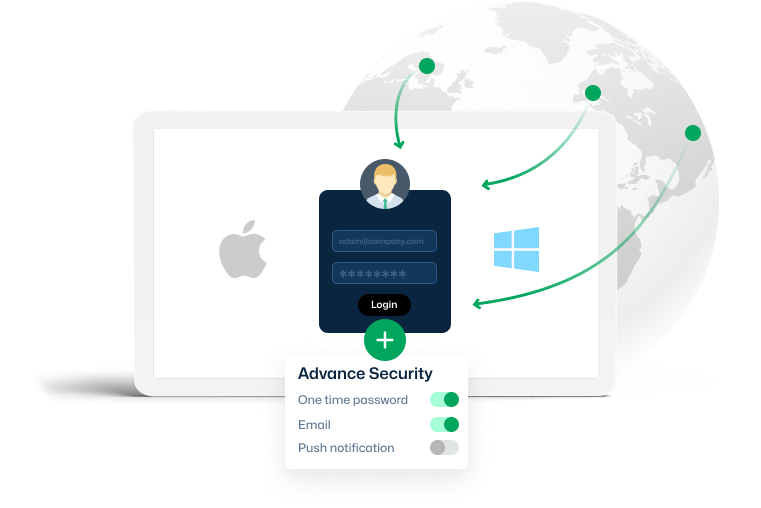

Trusted Browser
Deployment
Built-in MFA that comes out of the box!
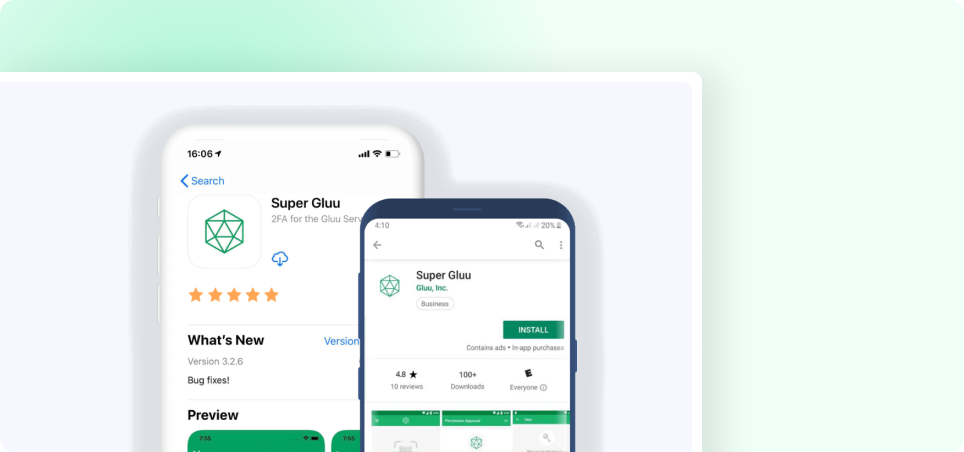
Super Gluu, a free iOS / Android App

FIDO / WebAuthn
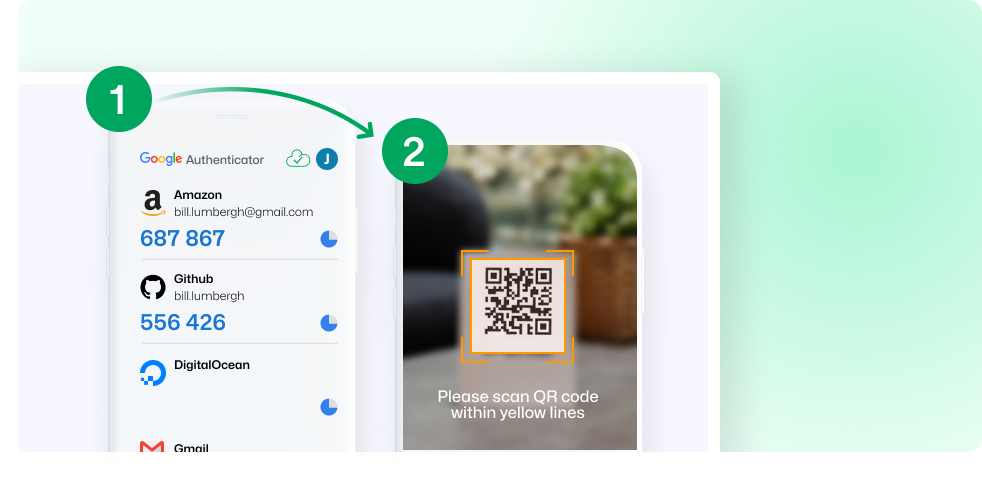
Google Authenticator
Plugins add More MFA options
Casa is a plugin-oriented, Java web application. Existing functionality can be extended and new functionality and APIs can be introduced through plugins.

BioID

Duo

Twilio
Twilio is an American company based in San Francisco, California, which provides programmable communication tools for making and receiving phone calls, sending and receiving text messages, and performing other communication functions using its web service APIs.
Streamline your communication capabilities with Twilio’s advanced suite of APIs.










