Enterprise security
signed and sealed...
with JWTs.
Open Standards
Solutions:
GovOps:
measure risk, transparency,
and accountability
With declarative policies, formal analysis, explicit federation, and continuous compliance, organizations can finally govern in real time — matching the velocity of the systems they are securing.
Built on Open Standards:
Capture every decision across your enterprise to enhance centralized threat detection and compliance.
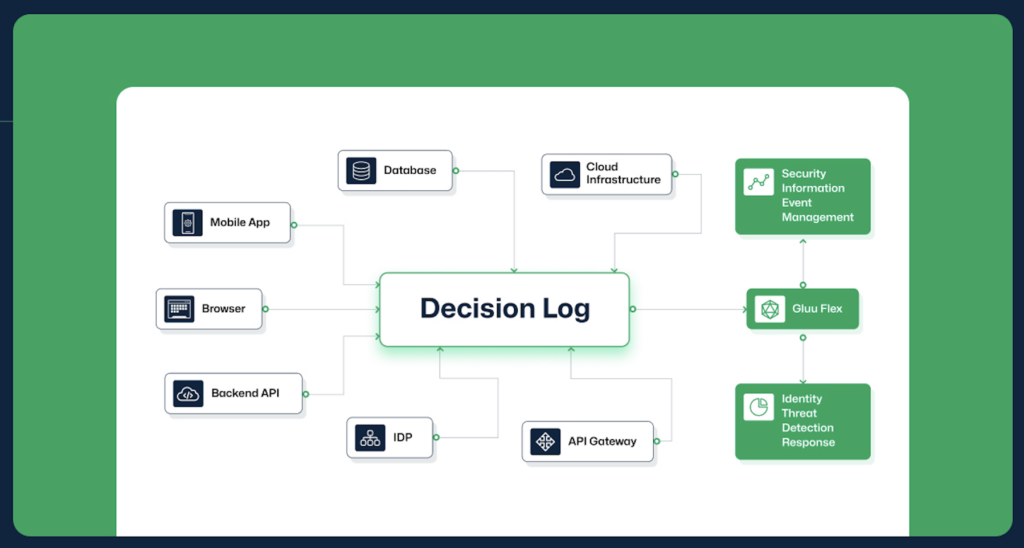
Collect Logs
Gluu Flex collects all Cedarling decision logs, detailing everything that was both allowed and denied from the edge to the database.
Connect Logs
Gluu Flex connects authz decision events to Identity Threat Detection and Response (“ITDR”) services for real time protection and fraud detection.
How does it work?

Author Policies
Developers and security architects author policies for each application in a Git repository.

Enrich Tokens
Issue JWTs with the minimal amount of data needed by the application.

Embed PDP
Use the Cedarling for authorization decision or instrumentation in all applications, guaranteeing consistent decision logs.

Respond To Threats
Efficient token revocation is now possible through OAuth Status Lists. Use the Cedarling to validate JWT signatures, contents, and status.

Author Policies
Developers and security architects author policies for each application in a Git repository.

Enrich Tokens
Issue JWTs with the minimal amount of data needed by the application.

Embed PDP
Use the Cedarling form authorization decision or instrumentation in all applications, guaranteeing consistent decision logs.

Respond To Threats
Efficient token revocation is now possible through OAuth Status Lists. Use the Cedarling to validate JWT signatures, contents, and status.
Components


01 Cedarling
An open source embeddable PDP that runs anywhere, returning authorization decisions based on declarative access policies.

02 Gluu Flex
Enterprise cloud infrastructure that connects Cedarlings, provides OAuth-based workload and person identity, mints JWT tokens and publishes keys.

03 Agama Lab
Developer portal to author Cedar schema and policies, define low-code web and native authentication workflows, and manage Gluu Solo hosted infrastructure.

04 Janssen Project
Upstream open source project at the Linux Foundation which drives long term innovation of the core infrastructure.
JWT Validation

Validate signatures
The Cedarling can rapidly validate signatures based on keys published by the issuer, and enforce the algorithm strength required by the enterprise.

Validate Contents
The Cedarling checks the required claims are present and validates some of the values, e.g. the expiration of the token.
Check Status
Validate that the JWT hasn’t been revoked by fetching the latest OAuth Status list from the issuer.
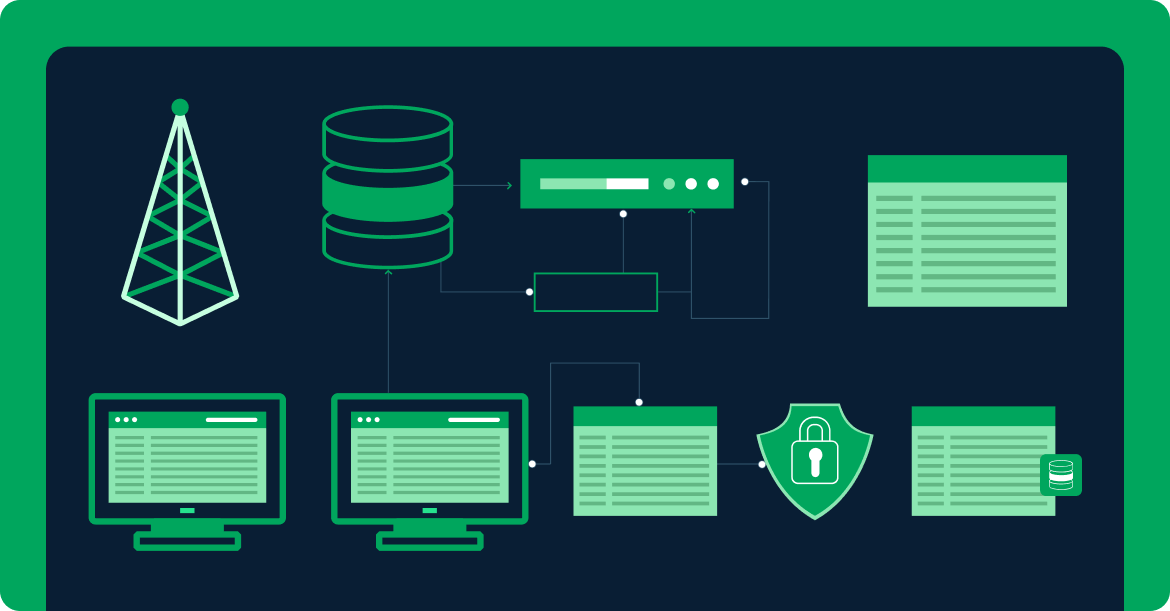
Built-in Security
Zero Trust from edge to edge: apps to databases
Enforce enterprise security policies and collect standard decision logs in each security context. At one edge we have the Internet, with mobile applications and browser-based applications. This is the most untrusted layer. At the other edge we have the database–it’s on the most protected network sement. For a complete security picture, enterprises need decision logs from the edges–and everything between.
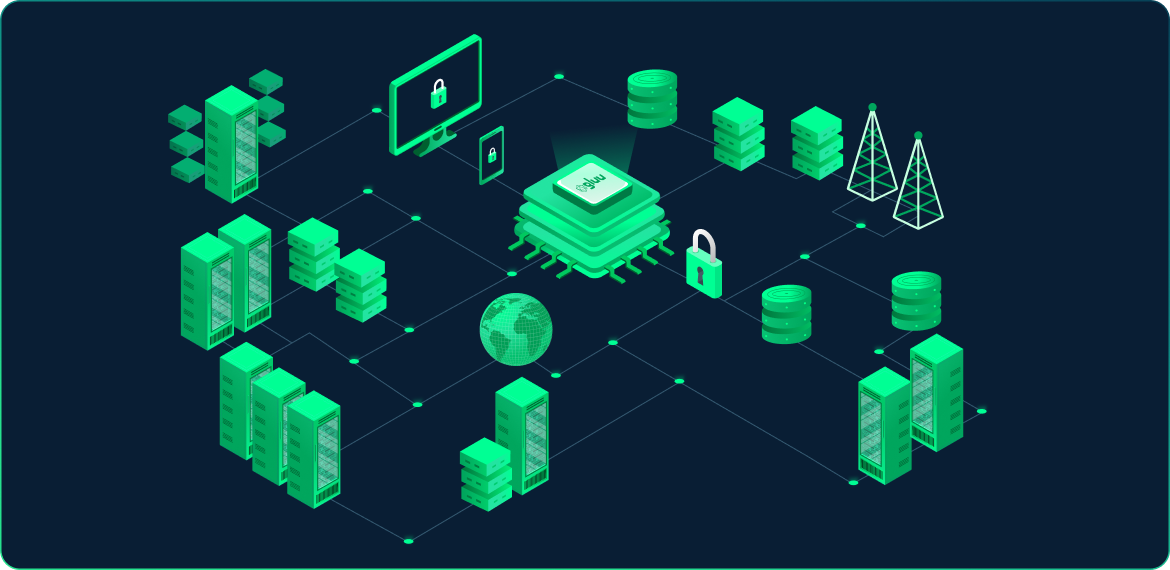
The Cedarlings log all decisions–allowed or denied. This rich source of information includes the tokens, policies, people, workloads, actions, resources, and context. These decision logs are vital input to threat detection infrastructure.
Gluu Flex streams data to SIEM and ITDR platforms for analysis and alerting. Gluu can call APIs for ITDR and SIEM SaaS vendors, providing the minimum required infromation to protect privacy and save costs.
Flex can can authenticate people and software, using customizable front channel or back channel flows. It can even do this post-authentication to gather consent or step-up authentication to satisfy enterprise policies to protect certain resources.
Flex provides real time telemetry information about the currently active Cedarling instances at the edge of the network.
CEDARLING Instrumentation
Legacy Application
Integration
The Cedarling provides a risk-free way to enhance security insights for legacy applications. By instrumenting applications, the Cedarling evaluates requests and logs decisions—without altering security behavior. Built for performance and flexibility, the Cedarling leverages Rust for fast execution, ensuring minimal impact on application performance. Security modernization doesn’t have to be disruptive.
CEDARLING PERFORMANCE
50 microsecond
decisions
Speed matters in enterprise security. The Cedarling typically delivers authorization decisions in under 50 microseconds. In the browser, mobile app, API gateway or database, the Cedarling’s Rust-powered engine guarantees lightning-fast access control. For enterprises where one millisecond means lost revenue, the Cedarling is the next-generation solution for secure, high-speed authorization.

Privacy-first access control
Application
Scoped JWTs
The JWT data payload is minimized and aligned with the least privlege to perform the task.
Application
Scoped Policies
Each application has its own policy store, leading to faster policy execution, simplified governance, and a reduced blast radius if breached.
Consent
Workflows
Flex supports post-authentication front channel and back channel user consent flows.
OAuth Transaction
Token Support
These new JWTs enable Users to delegate access with precise access instructions.
Hosted or Self-Hosted both supported
Flex License
$500
100 MAU
$1,750
400 MAU
$6,125
1,600 MAU
Solo Hosting
- Features
- Cost per location (month)
- Cost per location (year)
- Requests per month
- Max locations allowed
- vCPU
- RAM(GiB)
- Automatic Scale
- Replicas per location
- SLA
Cost per request
- Planet
- $800
-
$8,000
2 months free
- Up to 25M
- 3
- 4
- 8
- Yes
- Unlimited
- 99.9%
$0.000012
- Star
- $1500
-
$15,000
2 months free
- Up to 250M
- 10
- 4
- 8
- Yes
- Unlimited
- 99.9%
$0.0000022
- Galaxy
- $4,000
-
$40,000
2 months free
- Up to 2.5B
- 15
- 4
- 8
- Yes
- Unlimited
- 99.9%
$0.0000012
Hosting
- Planet
Want to purchase a plan? contact us and find out how.
- Features
-
Cost per location(month)
$500 -
Cost per location(year)
$8,000 2 months free -
Request per month
Up to 25M -
Max locations allowed
3
All features
-
vCPU
4 -
RAM(GIB)
8 -
Automatic Scale
Yes -
Replicas per location
Unlimited -
SLA
99.9% -
Cost per request
$0.000012
- Star
Want to purchase a plan? contact us and find out how.
- Features
-
Cost per location(month)
$1,500 -
Cost per location(year)
$15,000 2 months free -
Request per month
Up to 25M -
Max locations allowed
10
All features
-
vCPU
4 -
RAM(GIB)
8 -
Automatic Scale
Yes -
Replicas per location
Unlimited -
SLA
99.9% -
Cost per request
$0.000012
- Galaxy
Want to purchase a plan? contact us and find out how.
- Features
-
Cost per location(month)
$4.000 -
Cost per location(year)
$40,000 2 months free -
Request per month
Up to 2.5B -
Max locations allowed
15
All features
-
vCPU
4 -
RAM(GIB)
8 -
Automatic Scale
Yes -
Replicas per location
Unlimited -
SLA
99.9% -
Cost per request
$0.000012
Still have a question?
Schedule a call with to flush out if Gluu Flex makes sense for your business.
