Strong Protection in the Era of Rising Threats
Today’s cyberspace and IT systems have transformed from a uniformed homogeneous structure brought on by a fixed workspace and data center system to a heterogeneous network consisting of innovative technologies that enable the remote workforce with distributed work and office systems, mobile, and cloud-based systems.
In this new order, the classic perimeter of security concepts has begun to blur and open opportunities for attackers to carry out new cyber threats. The standard features of these threats occur independently of the network layer. In this case, firewall-oriented architectures, which are the basic building blocks of perimeter security remain unsolved. Legacy perimeter entry and exit points and security measures have been replaced by identity and authentication management (IAM) systems, especially in cloud-based systems, IAM has come to the forefront as the new perimeter.
Credential-based attacks against modern IT systems are on the rise. Credential- Access is one of the main tactics in the MITRE ATT&CK framework. Credential access consists of stealing credentials like account names and passwords. Techniques used to get credentials to include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.
One of the threat actor’s primary goals is the theft of an organization’s credentials. This could be particularly damaging, as the group could use the credentials, depending on the permissions associated with them, to gain access to other IT systems to infect more machines and deploy additional nefarious scripts.
Stolen credentials are one of three possible avenues of attack SolarWinds is investigating as it tries to uncover how it was first compromised by the hackers, who went on to hide malicious code in software updates that SolarWinds then pushed to some 18,000 customers, including numerous federal agencies.
Other theories SolarWinds is exploring, said SolarWinds CEO Sudhakar Ramakrishna, include the brute-force guessing of company passwords, as well as the possibility the hackers could have entered via compromised third-party software.
The Colonial Pipeline ransomware incident in May 2021 disrupted fuel supplies in the eastern US, though only IT systems and not the industrial control systems were reportedly affected. This resulted in canceled flights, caused fuel prices to temporarily increase, and led to rationing in some areas. The entry point for the attack was a password authentication-based VPN, for which the compromised password was found on the dark web.

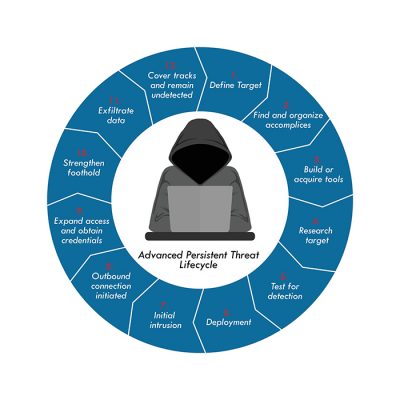
The Most Common Methods Threat Actors Use to Compromise an Account and Escalate to Identity
Interception
Passwords are captured as they are transmitted electronically through email, the network, and SMS texts. This includes SMS cloning, SIM jacking, other forms of hijacking, and man-in-the-middle attacks.
Interception involves the attacker interfering with a victim’s legitimate network by intercepting it with a fake network before it can reach its intended destination. The interception phase is essentially how the attacker inserts themselves as the “man in the middle.
Brute Force
A brute force attack uses a trial-and-error approach to systematically guess login info, credentials, and encryption keys. The attacker submits combinations of usernames and passwords until they finally guess correctly.
Once successful, the actor can enter the system masquerading as a legitimate user and remain inside until they are detected. They use this time to move laterally, install back doors, gain knowledge about the system to use in future attacks, and steal data.
Brute force attacks have been around as long as there have been passwords. They not only remain popular but are on the rise due to the shift to remote work.

Unsecured User Credentials
Adversaries may search compromised systems to find and obtain insecurely stored credentials. These credentials can be stored and/or misplaced in many locations on a system, including plaintext files (e.g., Bash History), operating system or application-specific repositories (e.g., Credentials in Registry), or other specialized files/artifacts (e.g., Private Keys).
Strong Authentication with Gluu
You don’t need to be pessimistic to protect your identity in the threat environment we have defined. Every problem has a solution. At this point, the solution is Gluu which makes your identity management secure with the vision of being the best and most secure open-source IAM for years. GLUU brings you the power of strong authentication against identity and access management systems or mechanisms.
Wouldn’t you rather stop a security breach than detect it? So why do organizations have a love affair with intrusion detection systems and neglect strong authentication? While an IDS system can detect a breach, the authentication may stop it entirely. Numerous surveys done over the years have shown that passwords are the most common cause of information security breaches.
Upgrading authentication may be the best investment you can make in enterprise security in terms of effectiveness. Fast identity online (FIDO) standards are authentication protocols where security and user experience meet. FIDO eliminates the risk caused due to password mismanagement as its cryptographic login credentials are unique for every website that is not stored on a server but stored locally on the user’s device.

The first three months of 2022 saw more than a million reported phishing attacks, according to the APWG’s Phishing Activity Trends Report. It’s the most phishing attack that has ever been reported in a quarter, and it follows a steady increase in attacks throughout the past year. In April 2021, the APWG observed just over 200,000 phishing attacks. By March 2022, it almost doubled, to 384,291.
Authentication is the front door to your organization. If you get it wrong, it will inhibit your ability to roll out new services. But, If you get it right, it will help you fend off impending attacks. Bring your organization into the future with passwordless authentication. New standards like the W3C Web Authentication API (WebAuthN) and Fast Identity Online (FIDO) are enabling passwordless authentication across platforms.
With Casa passwordless authentication you can make the login process easier by leveraging biometrics, security tokens, and mobile devices. Using these techniques, you can reduce the risk of stolen credentials and prevent phishing–the two most common ways hackers can get into your organization.
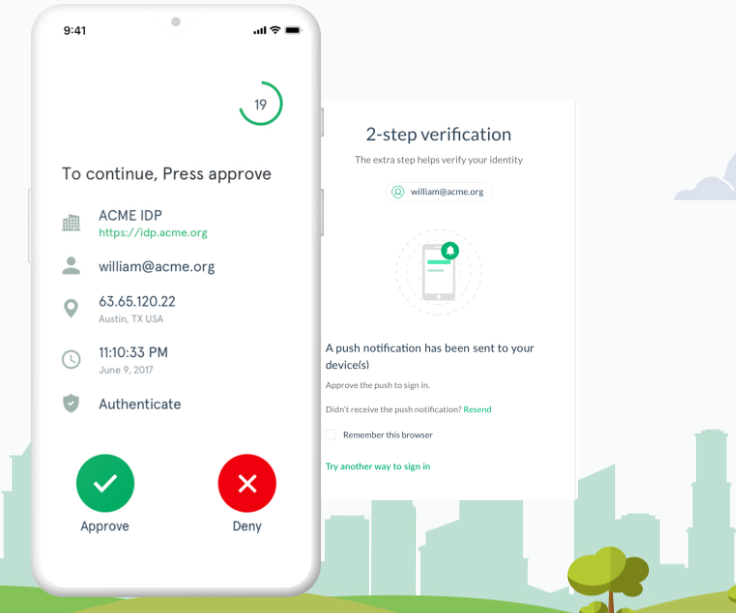
Multi-Factor Authentication (MFA)
Implementing MFA makes it more difficult for a threat actor to gain access to business premises and information systems, such as remote access technology, email, and billing systems, even if passwords or PINs are compromised through phishing attacks or other means.
Adversaries are increasingly capable of guessing or harvesting passwords to gain illicit access. Password cracking techniques are becoming more sophisticated and high-powered computing is increasingly affordable. In addition, adversaries harvest credentials through phishing emails or by identifying passwords reused from other systems. MFA adds strong protection against account takeover by greatly increasing the level of difficulty for adversaries.
Gluu ships with out-of-the-box support for many 2FA mechanisms, like FIDO, OTP, SMS, smart card, Duo, and many more. The Gluu Platform also offers a unique self-service portal called Casa, which enables end-users to manage their 2FA credentials, much like they would do at Google.
Super Gluu is a free and secure two-factor authentication (2FA) mobile app
- Super Gluu is tightly bundled with the Gluu
- Server identity and access management
- platform, and can be used to achieve 2FA
- for web and mobile applications that
- leverage Gluu for authentication.