A Secure Technical Implementation Guide (“STIG”) is a document published by the Department of Defense Cyber Exchange (DoD), which is sponsored by the Defense Information Systems Agency (DISA). It contains guidance on how to configure systems to defend against potential threats. These threats mainly include cyberattacks, but there can also be problems caused by the use of misconfigured systems.
The DISA STIG for Red Hat Enterprise Linux version 8 (“RHEL 8”) is published on Github. As there are 291 rules, implementation can be somewhat time-consuming. Luckily, while installing RHEL 8, you can select the DISA STIG security profile. This makes setting up a compliant server incredibly easy. Thanks Red Hat security team!
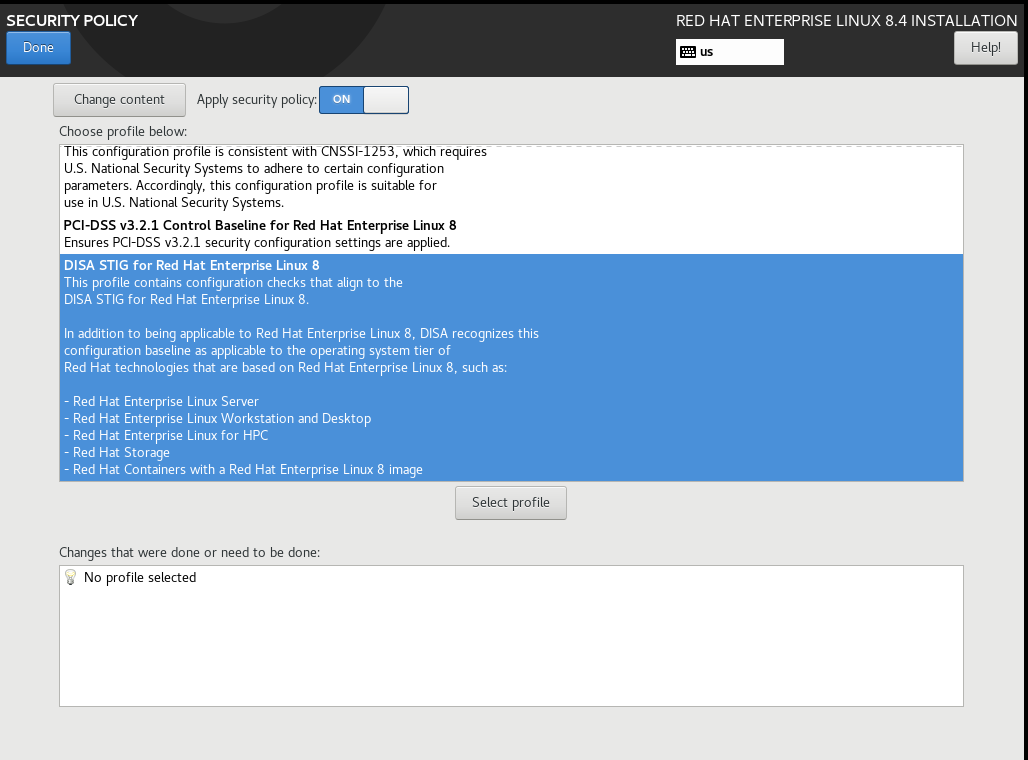
Some of the features of this security profile are more restrictive than a default RHEL 8 server. In particular, consider these three services:
- fapolicyd : A kernel-level enforcement process to control which users can access files
- SELinux : A kernel-level enforcement process to control which users can run a process or use a network port
- System-Wide Cryptographic Policies : A mechanism to enforce minimum cryptographic algorithm strength for system services
Gluu publishes a specific .rpm package for deployment on RHEL 8 DISA STIG profile servers. This “FIPS” distribution has a few differences:
- Bouncy Castle FIPS certified cryptographic libraries
- Bouncy Castle Foundation KeyStore format (BCFKS) instead of JKS
- No Shibboleth SAML IDP (coming soon!)
- No Passport-JS (handle social login from interception scripts instead)
- LDAP only
- “no-chroot” distribution
- Only FIPS supported cryptographic algorithms
If you want to try Gluu Server 4 on a Red Hat server, folow the instructions below!
RHEL 8 Installation
Before you install the Gluu Server, you’ll need to do a base installation of RHEL 8. Below are some hints about how to do this right the first time:
1. Select “Minimal Software” installation
2. Manually partition your disk
| /tmp | 1G |
| /boot | 500M |
| /home | 3G |
| /var | 5G |
| /var/log | 3G |
| /var/log/audit | 2G |
| /var/tmp | 1G |
| / | (rest of the space) |
3. Select DISA STIG Security Profile (see above screenshot)
4. Set a FQDN hostname; Enable network
5. Activate subscription to the RHEL package repository
$ sudo su -
# subscription-manager register
Username: (your acct name)
Password: *******
# subscription-manager attach --auto
# yum upgrade
6. Open ports for http and https
HTTP just redirects to HTTPS, but opening the port prevents some confusion by end users.
# firewall-cmd --zone=public --permanent --add-service=https
# firewall-cmd --zone=public --permanent --add-service=http
# firewall-cmd --reload
Installing the Gluu Server
Like all Gluu Server 4 distributions, all components are open-source, and the binary is freely available. If your organization is interested in deploying a highly available cluster of these servers, you should reach out for more information about a VIP support subscription.
1. Install the Gluu package GPG Key
# wget https://repo.gluu.org/rhel/RPM-GPG-KEY-GLUU -O /etc/pki/rpm-gpg/RPM-GPG-KEY-GLUU
# rpm --import /etc/pki/rpm-gpg/RPM-GPG-KEY-GLUU
2. Install the Gluu Server package
You can either install with dnf :
# wget https://repo.gluu.org/rhel/Gluu-rhel8.repo -O /etc/yum.repos.d/Gluu.repo
# dnf install gluu-server-nochroot-fips
Or download the rpm directly
# wget https://repo.gluu.org/rhel/8/gluu-server-nochroot-fips-4.4.1-el8.x86_64.rpm
# dnf install ./gluu-server-nochroot-fips-4.4.1-el8.x86_64.rpm
3. Run Setup
# cd /install/community-edition-setup
# ./setup.py
Make sure you enter an FQDN for the `Hostname` during setup. Install all components. Use the Authorization Server’s persistence mechanism for oxd
4. Verify Installation
# /sbin/gluu-serverd version
On your local desktop, add the Gluu Server hostname for `127.0.0.1`. Then create an ssh tunnel between the Gluu Server host and your desktop. In the example below, replace *10.10.10.10* with the ip address of the Gluu Server:
$ ssh -L 2221:10.10.10.10:22 -L 443:10.10.10.10:443 user@10.10.10.10
Once your port forward and local hostname is setup, you can navigate to the Gluu Server Administration web interface by entering https://{hostname} into your browser. To navigate to Casa, the URL is https://{hostname}/casa.
The default, an out of the box installation of Gluu Server 4 creates a self-signed web certificate. If you are using Chrome, ou may need to type “thisisunsafe” in the browser to bypass the warning page.
If all goes well, you should see the Gluu Server 4 admininstration web site: