Single Sign-On (SSO) to Salesforce.com#
By default Salesforce suggest deployers to implement IDP-initiated SSO. The initialization of IDP-initiated SSO is little bit complex as it requires a big hostname which includes IDP's SSO link as well as SP's login uri. So we prefer SP-initiated SSO and here in this documentation we are presenting a very simple SP-initiated SSO steps with Salesforce and Gluu Server. Still, you can go for IDP-initiated SSO if you prefer. Further documentation is available at the Salesforce.com site.
Prepare Salesforce.com#
- Log into Salesforce.com with your administrative account.
- Click on Setup in the right upper corner of the page.
- You need to add a custom domain name for your Salesforce.com site if you do not have any yet.
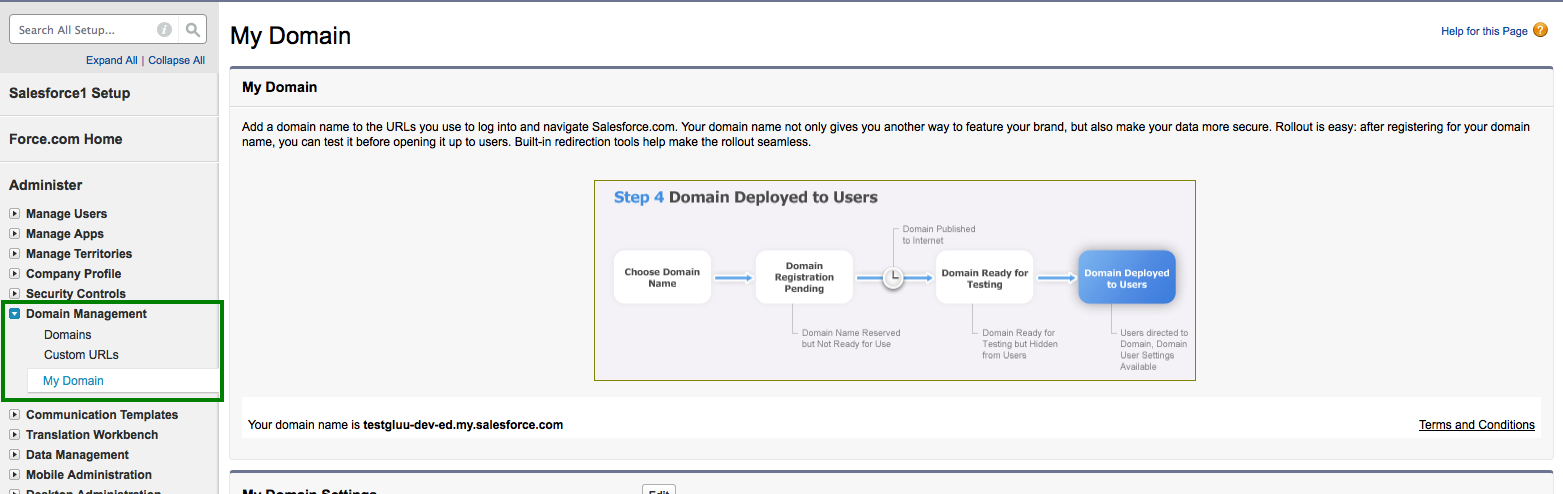
- Go to
Domain Management>My Domain - Add your custom domain
- Wait for some time. Salesforce.com will register this domain name
for you. As an example we use
testgluu-dev-ed.my.salesforce.comhere.
- Register your Gluu Server information in Salesforce.com
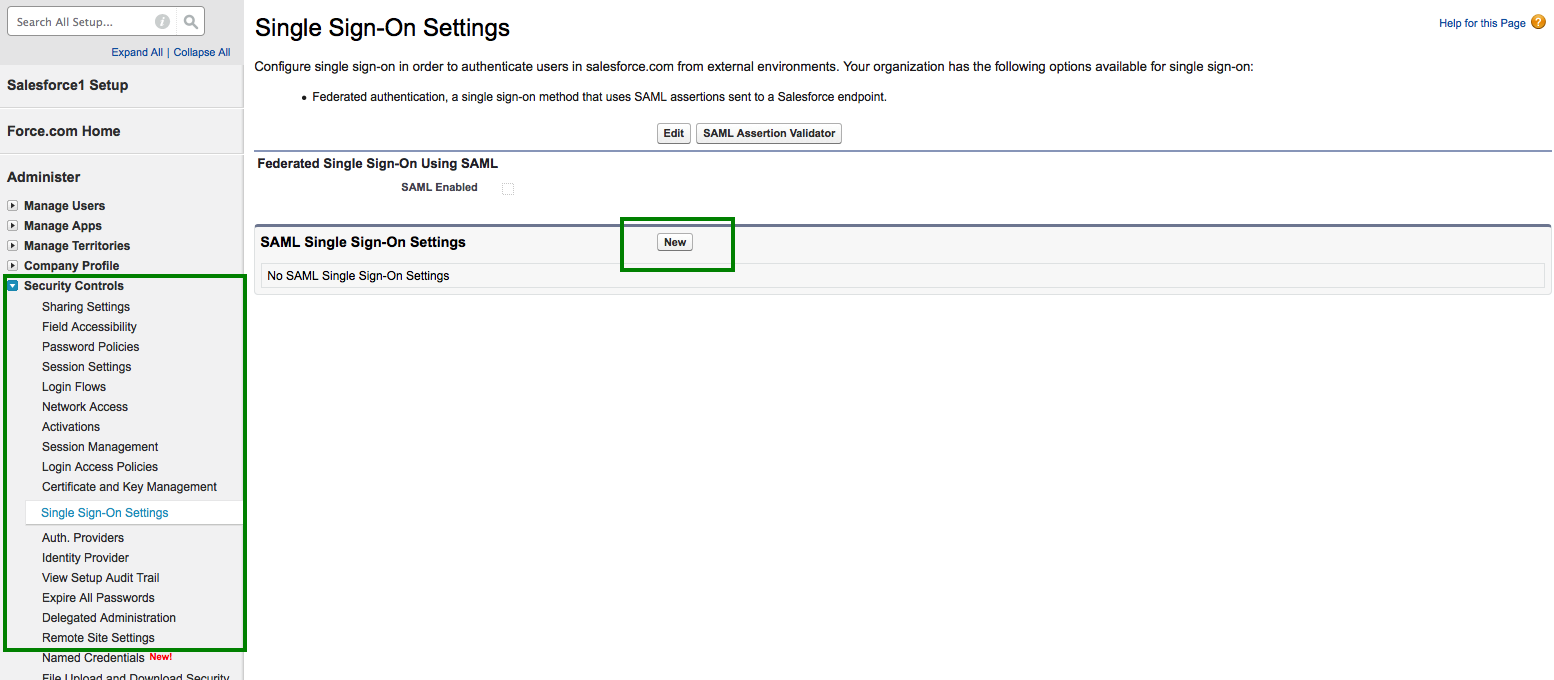
- Go to
Security Controls>Single Sign On Settings - Click
New
-
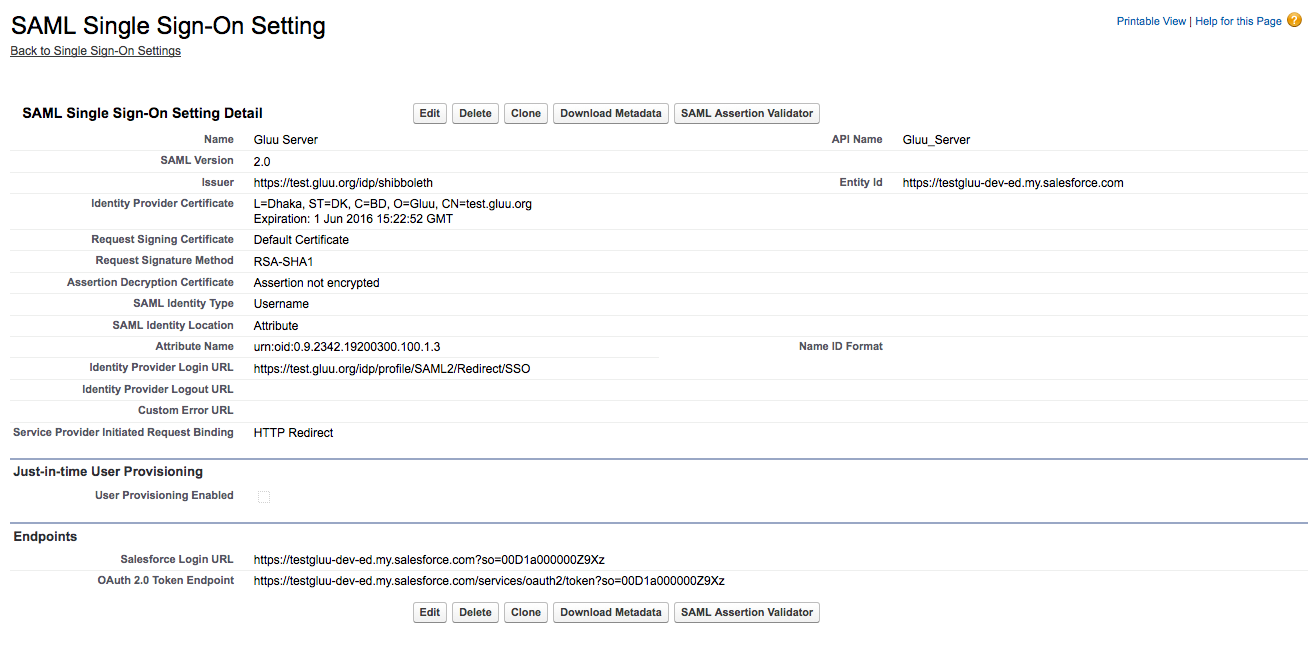
Now you need to add the information of your Gluu Server here
- Name: Anything, whichever is easier for you to recognize this
setup, i.e.
Gluu Server - API Name: Gluu Server.
- Issuer: EntityID of your Gluu Server, i.e.
https://test.gluu.org/idp/shibboleth - EntityID: Your Salesforce.com custom domain name as chosen
above, i.e.
https://testgluu-dev-ed.my.salesforce.com - Identity Provider Certificate: Grab your Gluu Server's SAML certificate. SAML certificate can be grabbed from your Gluu Sever's metadata. Save the certificate and upload it.
- Request Signing Certificate: Default certificate
- Request Signature Method: RSA-SHA1
- Assertion Decryption Certificate: Assertion not encrypted.
- SAML Identity Type: Assertion contains user's Salesforce.com username
- SAML Identity Location: Identity is in an Attribute element
- Attribute Name: Provide 'SAML2 URI' of your attribute. For our test case we are using Gluu Server's Email attribute. How to check the information of your attribute is available here.
- NameID Format: Leave this field empty.
- Identity Provider Login URL:
https://test.gluu.org/idp/profile/SAML2/Redirect/SSO - Service Provider Initiated Request Binding: HTTP-Redirect
- Here is how our example setup looks like:
- Name: Anything, whichever is easier for you to recognize this
setup, i.e.
Prepare Gluu Server#
- How to create SAML trust relationship is available here.
- Grab Salesforce.com metadata from the Salesforce.com website. There is
an option named
Download Metadata: - Modify Salesforce.com metadata a bit:
- Remove
AuthnRequestsSigned=“true”from metadata. - Save metadata
- Remove
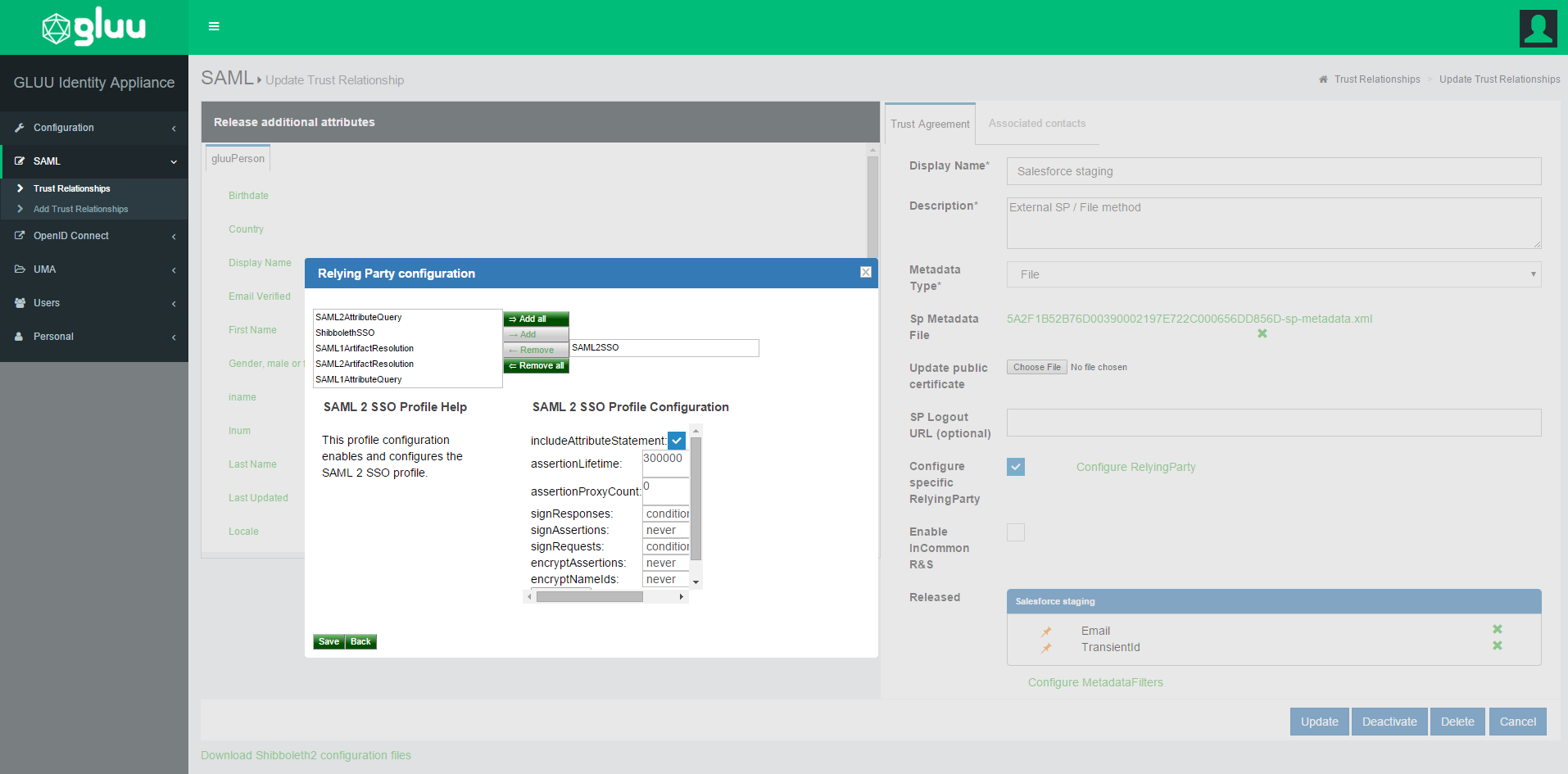
- Create Trust Relationship:
- Display Name: Anything, whichever is easier for you to recognize this trust relationship.
- Description: Anything, whichever is easier for you to recognize this trust relationship
- Metadata Type: 'File'
- Upload salesforce's metadata (your modified one)
- Releases attributes: TransientID and Email
- 'Add' this trust
- Configure Specific Relying: It can be done from Gluu Server's GUI (named: oxTrust)
- Select
SAML2SSO- includeAttributeStatement: Enabled
- assertionLifetime: keep the default one
- assertionProxyCount: keep the default one
- signResponses: conditional
- signAssertions: never
- signRequests: conditional
- encryptAssertions: never
- encryptNameIds: never
- Save it
- Select
Updatethe trust relationship- Here is how it looks like in our example setup:
Test SSO#
- Log in to Salesforce.com setup
- Click
Security Controls>Single Sign On Settings - Enable
Federated Single Sign-On Using SAML - Go to
Domain Management - Configure
Authentication Configuration - Select
Gluu Server - Save it
-
Here is how the
Authentication Configurationlooks like: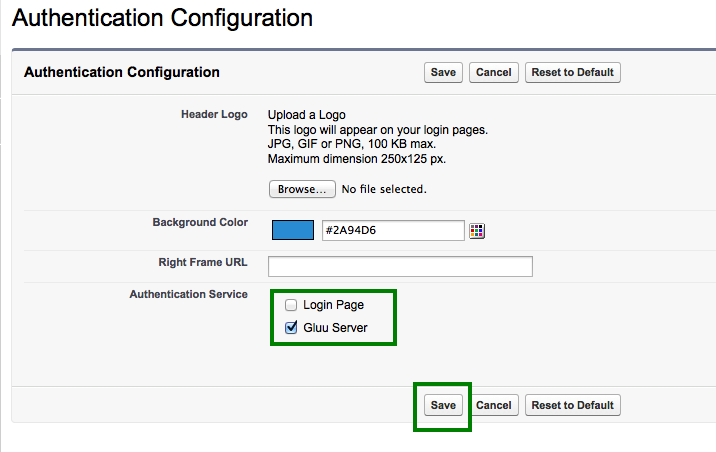
!!!Note: This is a SP-initiate SSO. SSO needs to be initiated from Salesforce.com.
Salesforce Demo Video#
You can watch a video demo of this SSO Here .