Policy Designer
Policy designer tool provides you a visual editor to build, manage, and test authorization policies written in Cedar language. Policy designer helps you quickly test these policies to authorise users based on tokens using Jans Cedarling.
You can use policy designer to:
- Create and manage policy stores that store multiple Cedar policies in a GitHub repository
- Create Cedar schema and policy using a visual editor
- Import Cedar schema and policies
- Validate policies against a given schema
- Test Token based authorisation control scenarios using Jans Cedarling
Key Features
Policy Store
Policy designer uses a GitHub repository designated by the user for storing details about schema, policy files etc. Using GitHub repository enables proper version control and release management of the changes in the policies and schema.
Policy designer stores these details in a grouping called Policy Store. Essentially, a policy store is a directory in a GitHub repository with schema and policy details in it.
One GitHub repository can have multiple policy stores. Each policy stores can have multiple policies and schema with multiple namespaces.
Wizard based editors
Policy designer allows you to write policies and test scenarios using step-by-step wizard. This further reduces learning curve around writing Cedar policies by hand and makes it less error prone.
Policy Wizard
Test Wizard
Detailed Walkthrough
Dashboard
Policy designer dashboard lists policy stores available in the repository. When the user has not selected the repository yet, the dashboard shows instructions for GitHub integration and repository selection as shown below:
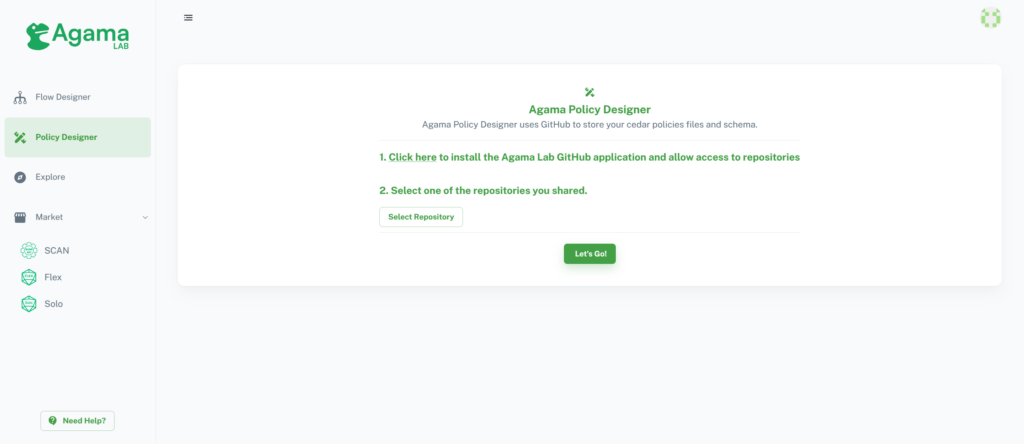
After successful GitHub integration, the user can select a repository by choosing the appropriate option.
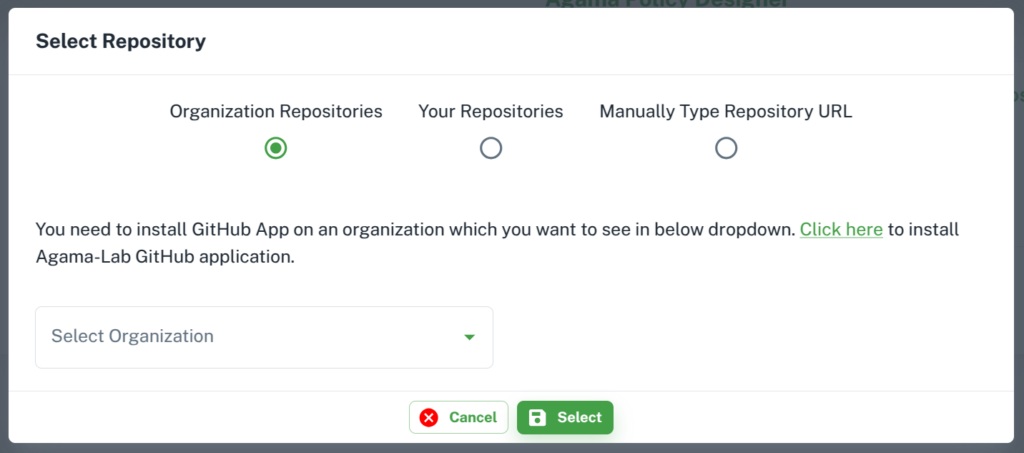
Once the repository has been selected, the dashboard will automatically load the stores from GitHub. Now the user can create new store as well.
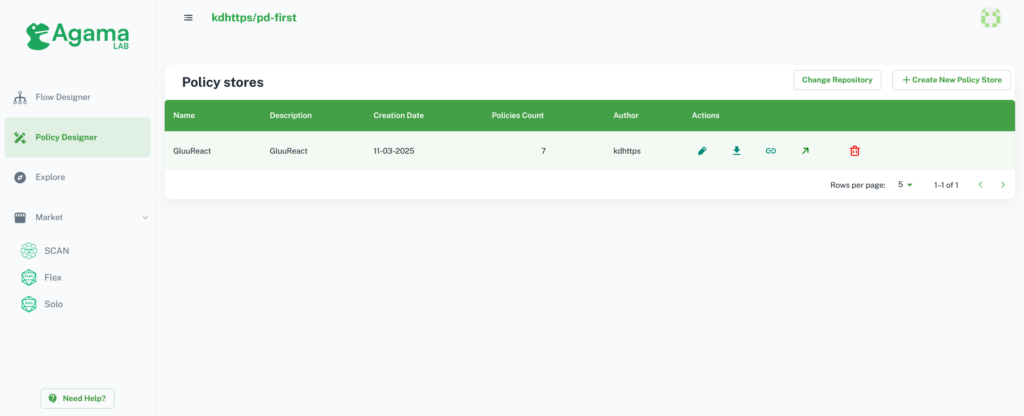
There are some quick access tools available in the list.

- Edit: used to edit store
- Download: used to download the store in JSON form, which you can directly use in Cedarling authorization
- Link: used to copy store GitHub link which you can use in Cedarling authorization
- Manage: used to manage store schema, policies, trusted issuer, and test policies.
- Delete: used to delete store
Schema Section
Click on the Manage button on the Store List, it will navigate you to the store manage page. Once you create a store, Agama Lab creates one default schema for you, which you can easily modify in the schema section.
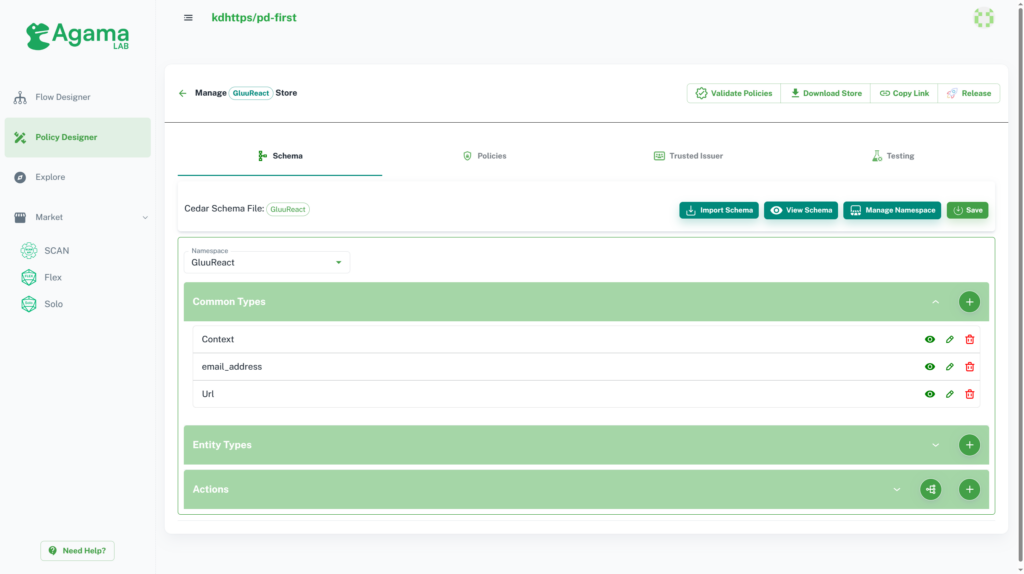
Manage Namespace
Click on Manage Namespace button and you will get the following option:
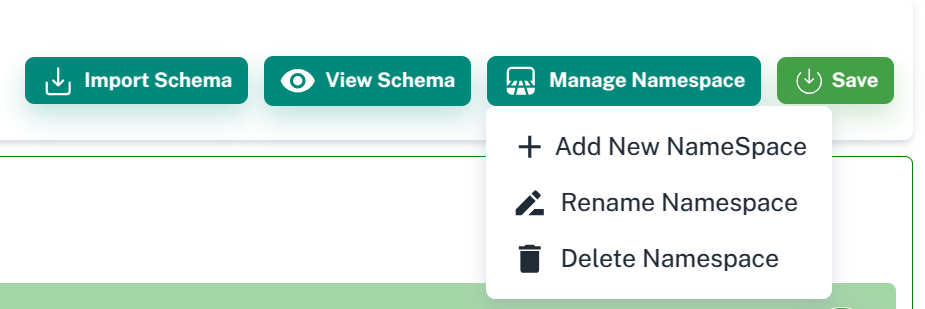
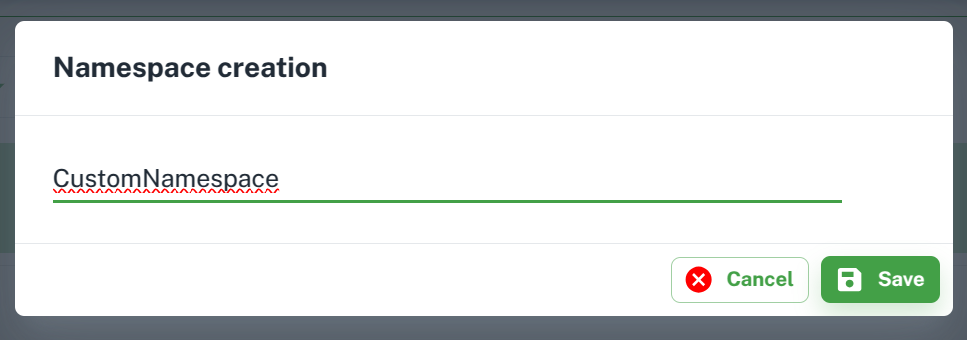
Add namespace
Select + Add New Namespace option from Manage Namespace to add a new namespace. It will open a dialog box for you to enter the new namespace name. Just enter a custom name and click on save to make a new store.
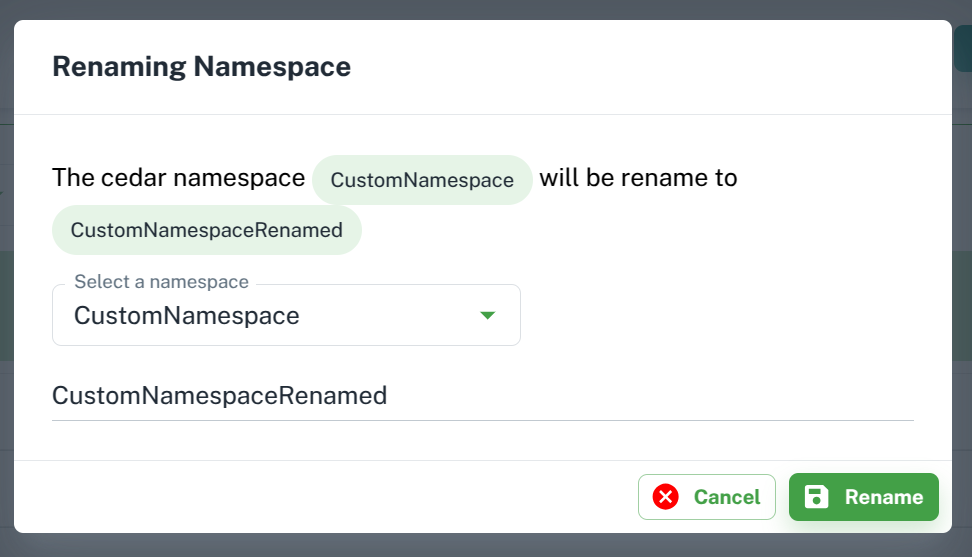
Rename namespace
Select Rename Namespace option from Manage Namespace to rename namespace. In the rename dialog box, select the namespace and enter a new name to replace the name.
Delete namespace
Select Delete Namespace option from Manage Namespace to delete the namespace. In the delete dialog box, select the namespace to delete it.
Import Namespace
If you already have the Cedar JSON Schema, then you can easily import it and save it in the policy store. Click on Import Schema button and select file.
View Schema
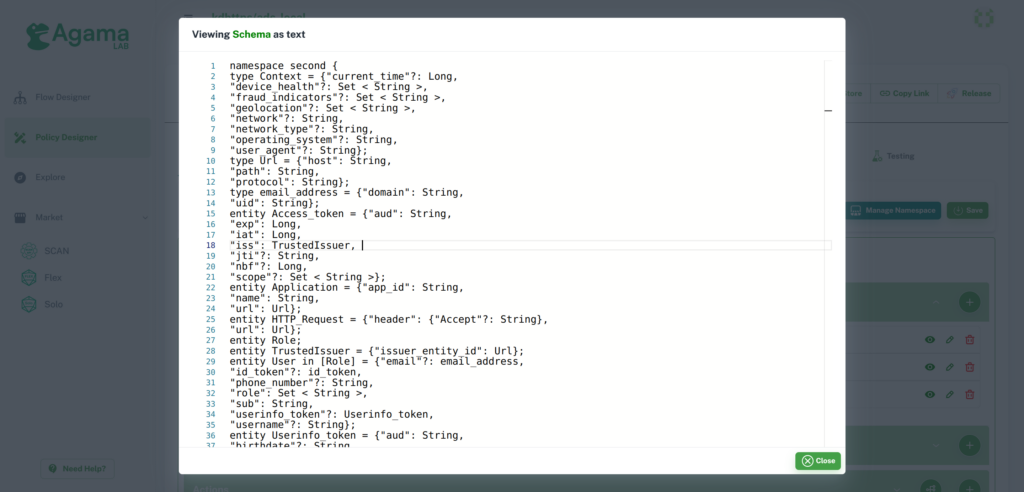
Use this feature to see your schema in JSON and Text format.
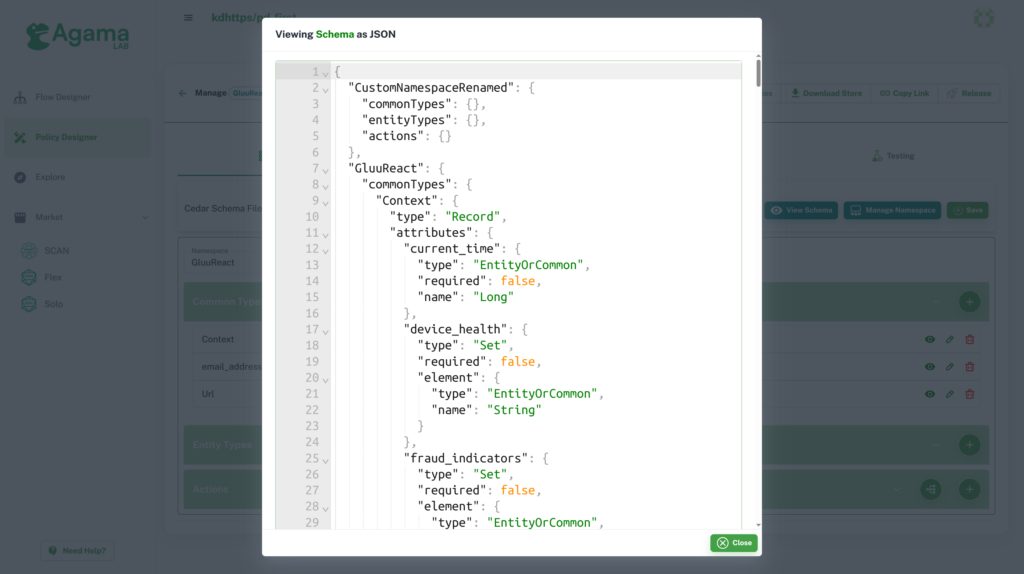
Example of schema JSON view:
Example of schema Text view:
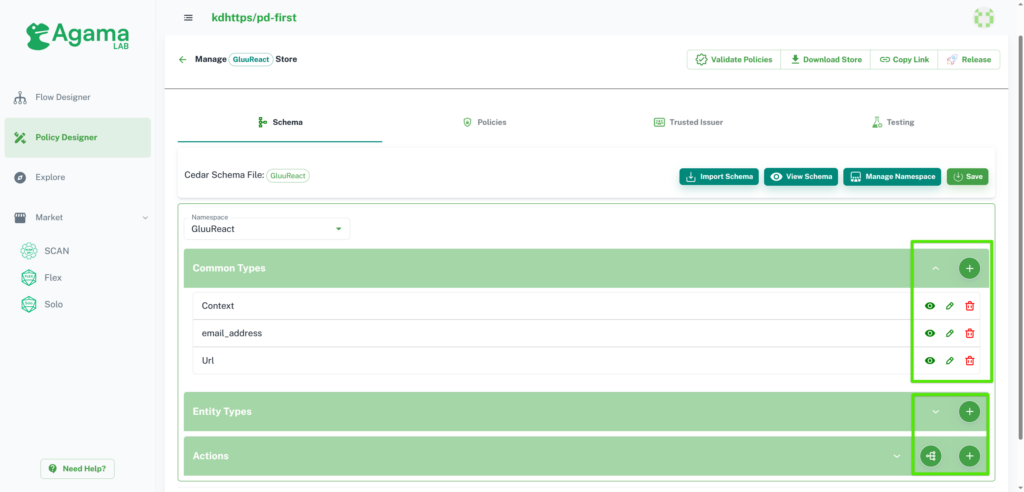
Update and Delete Schema Elements
There are options in UI where you can easily view, update and delete schema elements like Common Types, Entities, and Actions.
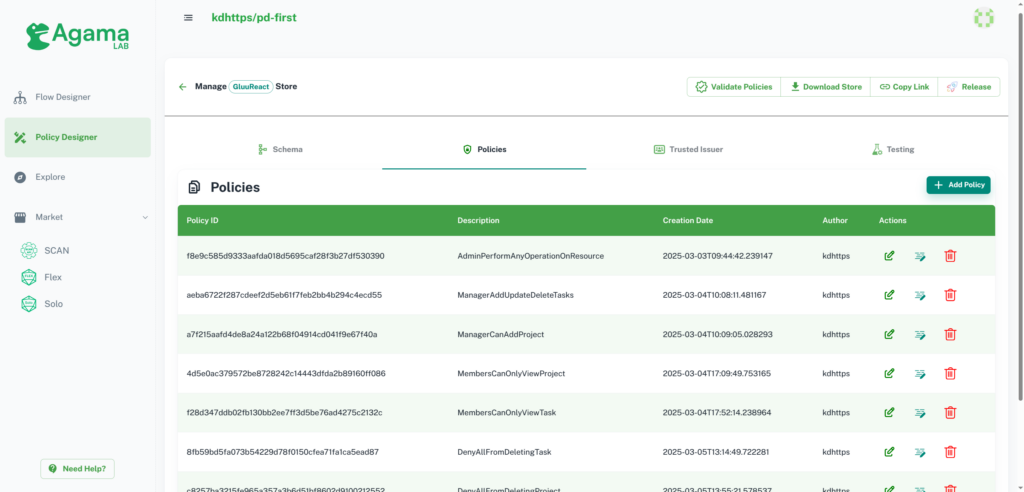
Policies Section
This section helps you to view, add, update, and delete policies. You can see your list of policies and there are Actions to manage policies.
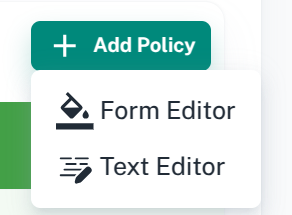
Policy Creation
There are 2 options to create a policy.
Text Editor
This option is simple to use. Click on Add Policy > Text Editor option. It will open a dialog box, write your policy, and Save the policy.
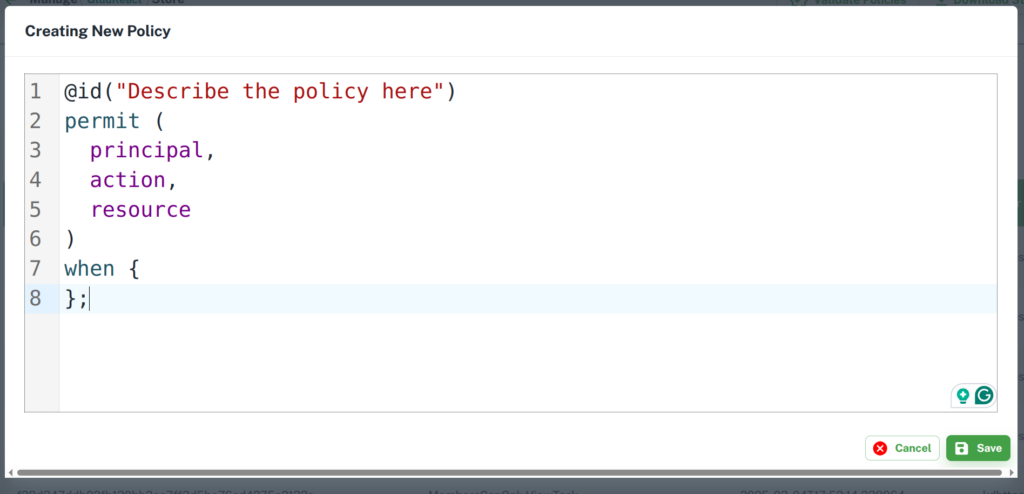
Form Editor
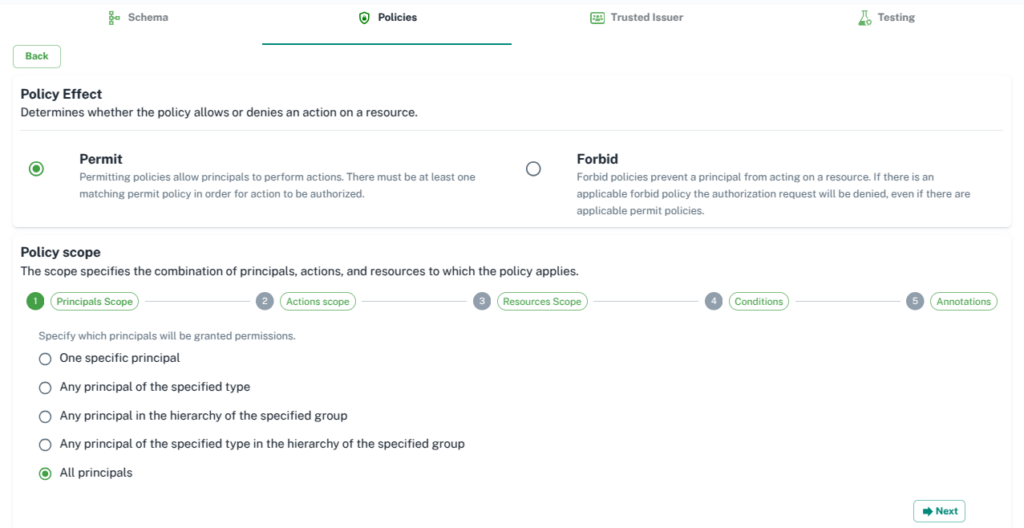
Writing a good and complete Cedar policy is an expert’s job, but the form editor provides a simple UI to easily write complex Cedar policies.
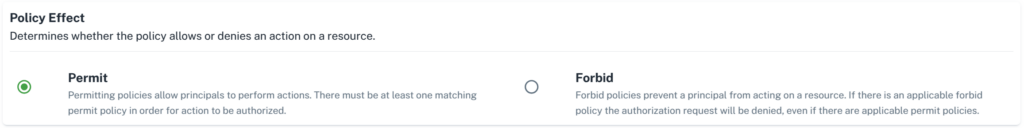
- First step is to select Policy Effect. Whether you want to
PermitorForbidpolicy as per your requirements.
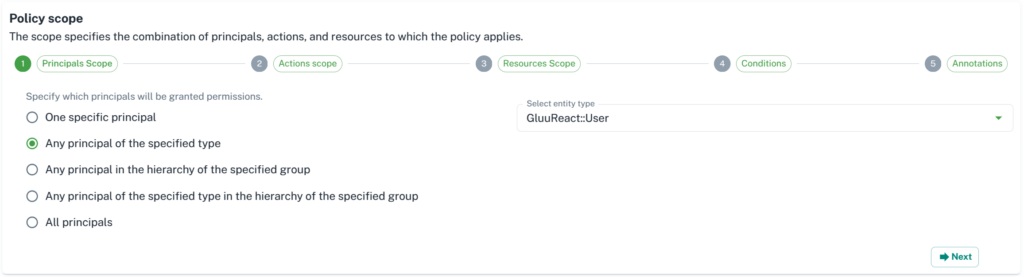
2. Second step is to add principal for your policy. There are several options. Choose as per your need.
3. Click on Next and it will take you to Actions scope.
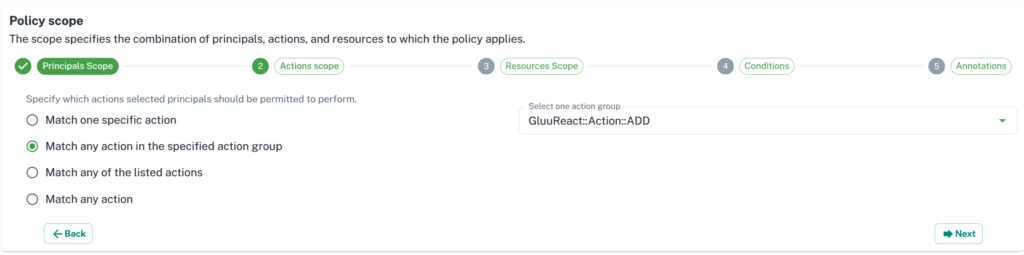
4. Next step is to add a resource for your policy.
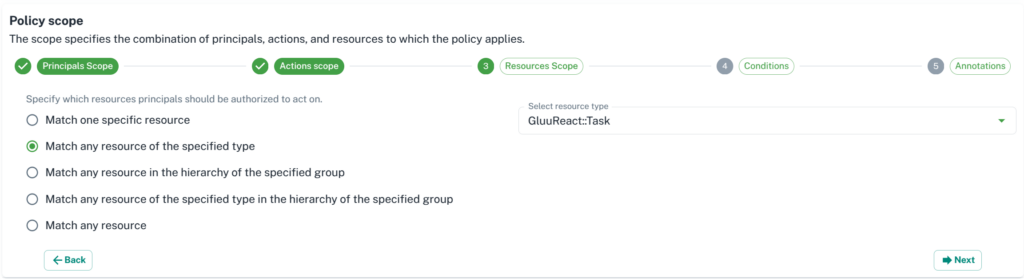
5. Next step is to add a condition. This is optional. You can use it to make an ABAC(Attribute-based access control) policy. Check button will help to validate the condition.
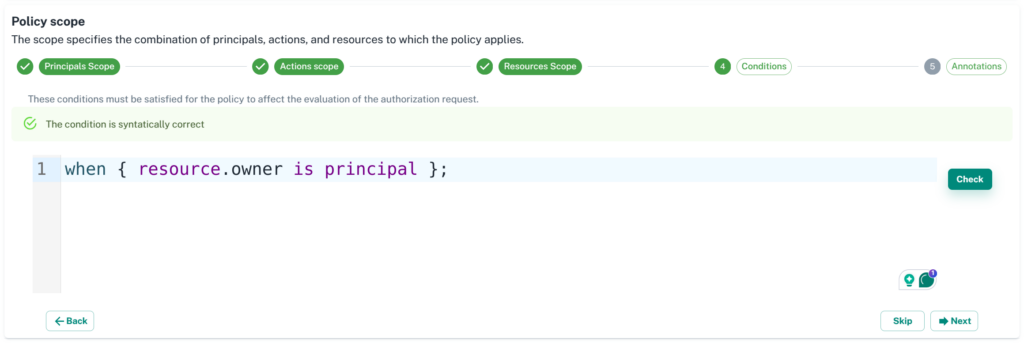
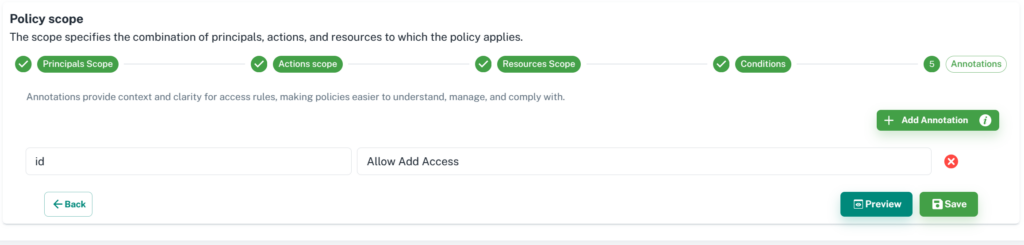
6. Last step is to add a description about your policy. At this step, you can preview and save the policy. Once you save the policy, you can see the policy and store the content on your selected GitHub repository.
Click on Preview button to see JSON Policy.
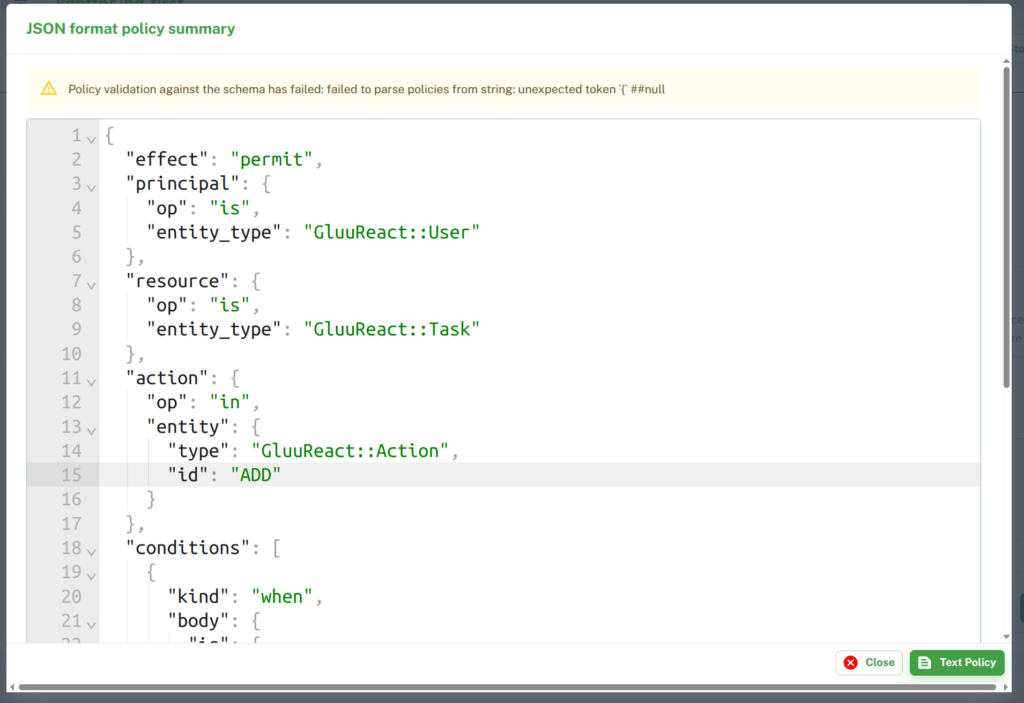
On policy dialog box, click on Text Policy to see human readable format of policy.
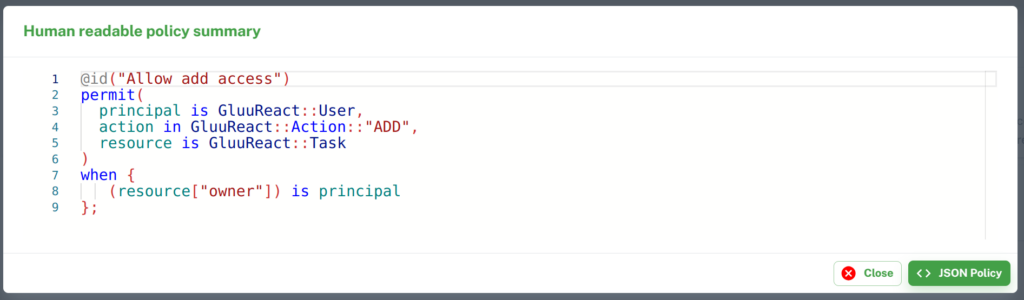
Trusted Issuer Section
In jans-cedarling there are some more features like token validation. For token validation, you need to register your Trusted Issuer(IDP) to validate token. Jans-Cedarling will also use this config to map tokens with cedar entities that are used during cedar authorization.
You can see your list of Trusted Issuers and there are Actions on this section.
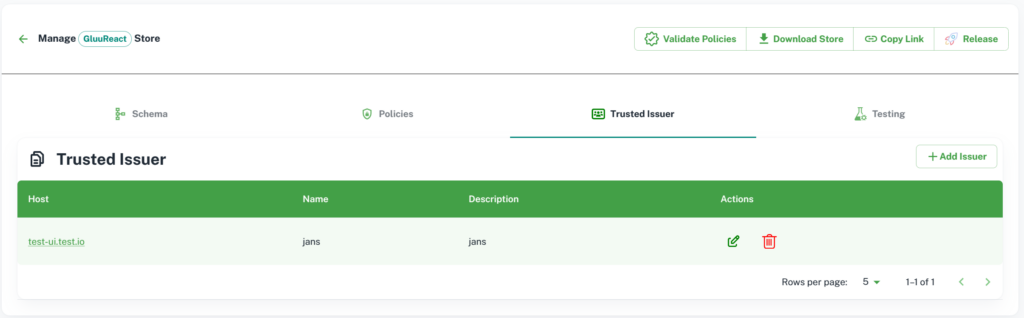
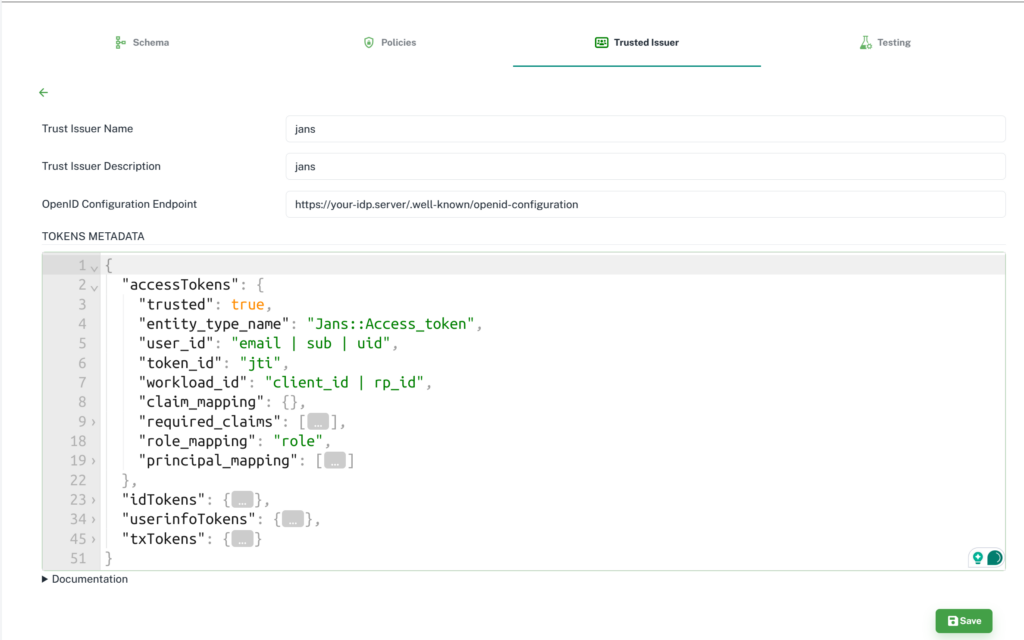
Click on Add Issuer to add a new issuer. The tokens metadata is important to map tokens with the cedar entities. More Details
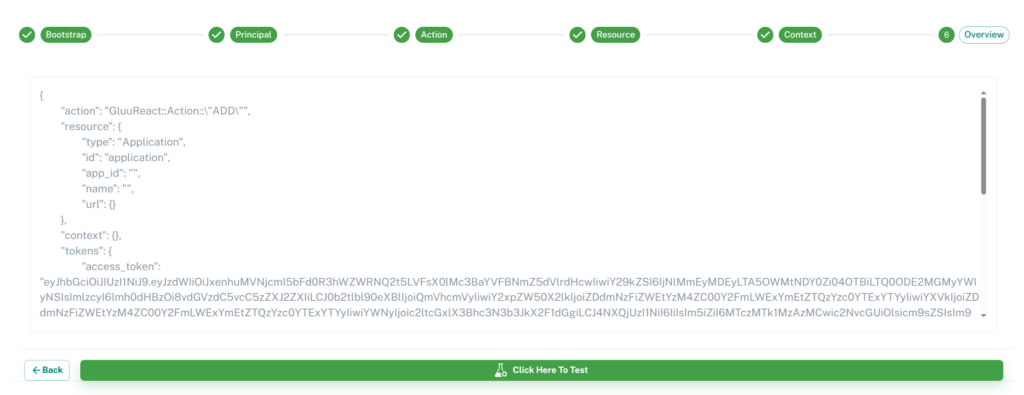
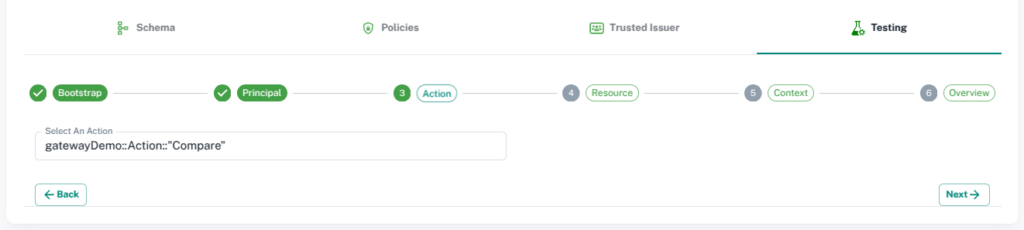
Testing
This feature will help you to quickly test your policy with your tokens and requested data. You can easily pass custom data that helps to test all your cases and save time. Agama Lab uses Jans Cedarling WASM to test requested in this section.
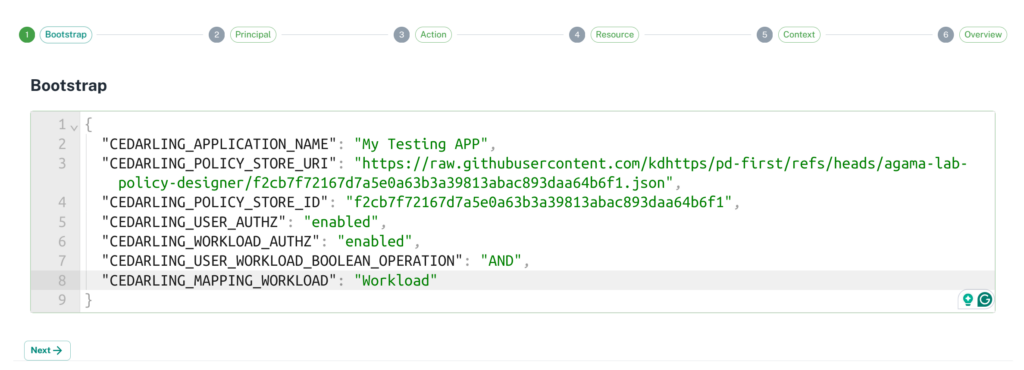
- First step is to set initial settings for cedarling-wasm. Check here for details about settings.
2. The second step is to set the Access Token, ID Token, and Userinfo token that you want to authorize.
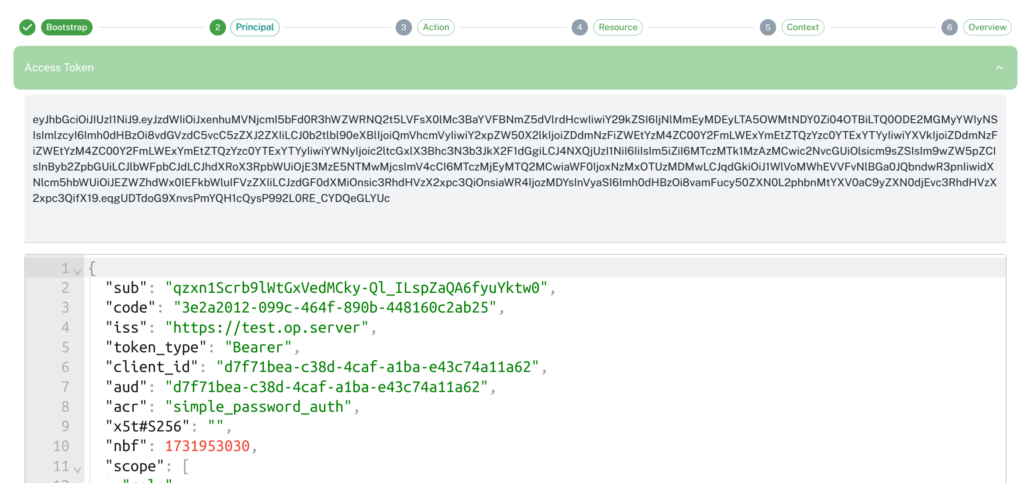
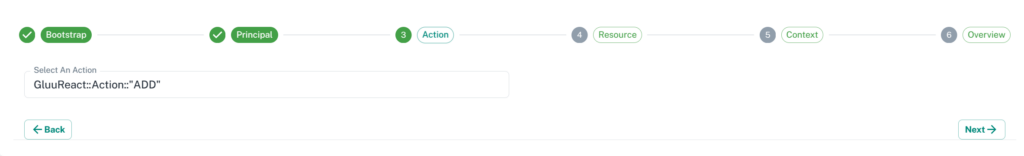
3. Third step is to set Action
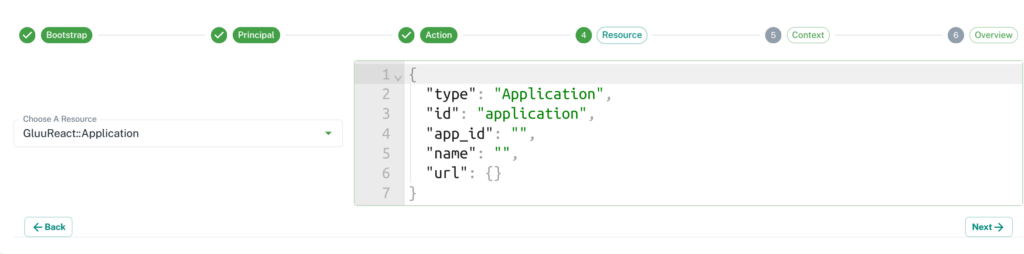
4. Fourth step is to set the Resource
5. In the fifth step, you can set context
6.In the last step, you can see the whole request which will be sent to Jans Cedarling. Click on Test button to authorize request.