User Registration
User Registration#
The Gluu Server is shipped with a user registration script that implements a very basic user registration process.
In most situations, we recommend writing a custom registraton app and then using Gluu's SCIM 2.0 endpoints to send the identity data to Gluu. Using SCIM will give you more control and flexibility over the registration process. Also, since oxTrust is frequently not Internet facing, the registration page (https://<hostname>/identity/register) may not be available to a user on the web.
Instructions for using Gluu's user registration functionality follows:
Enable User Registration#
To enable user registration via the Gluu Server, follow these steps:
- Navigate to
Custom Scriptsand select theUser Registrationtab; - Find the
Enabledfield and check the box; - Click the
Updatebutton at the bottom of the page; - New users will now be able to register for accounts at:
https://<hostname>/identity/register.
Note
When user registration is handled via oxTrust, users cannot be added to a backend LDAP or Active Directory server. This means that self-registration via oxTrust is only effective if users are authenticated by Gluu's LDAP (and not a backend LDAP or AD server).
Adding Attributes to Registration#
A limited number of attributes are present in the default registration form. If more attributes are needed, they can be added via the GUI by navigating to Organization Configuration > Manage Registration. Learn how to add attributes to the default registration form.
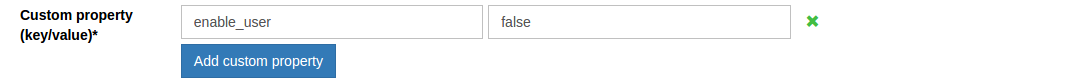
Manual Approval of New Users#
By default, the Custom property (key/value) field will include the value: enable_user and true. This enables new users to log in as soon as registration is complete. If you want to manually review and approve new user registrations, you can set this value to false as shown in the screenshot below.
Enforcing Unique Email Addresses#
Administrators can choose whether they want to require all users to have unique email addresses. Uniqueness is enforced by default. If this feature is disabled, more than one user can register the same email address. If a password reset is requested using a shared email address, the first matching user listed in LDAP will receive the reset email.
To change this setting, you need to make the following changes in both oxTrust and the LDAP:
oxTrust#
- Log in to the Gluu Admin UI
- Navigate to
Configuration>JSON Configuration - Select the
oxTrust Configurationtab - Select the appropriate option in the
enforceEmailUniquenessfield - Save
OpenDJ#
- Log in to the Gluu container with
service gluu-server-3.1.8 login - Run this command to list all plugins:
/opt/opendj/bin/dsconfig -h hostname -p 4444 -D "cn=directory manager" -w yourPassword -n list-plugins - To disable the email uniqueness plugin, run this command:
/opt/opendj/bin/dsconfig -h hostname -p 4444 -D "cn=directory manager" -w yourPassword -n set-plugin-prop --plugin-name "Unique mail address" --set enabled:false - If you want to re-enable the email uniqueness plugin, run this command:
/opt/opendj/bin/dsconfig -h hostname -p 4444 -D "cn=directory manager" -w yourPassword -n set-plugin-prop --plugin-name "Unique mail address" --set enabled:true - Restart OpenDJ: service opendj restart
OpenLDAP#
- Log in to the Gluu container with
service gluu-server-3.1.8 login - Open
/opt/symas/etc/openldap/slapd.confin a text editor - To disable email uniqueness, comment out the following line:
unique_uri ldap:///?mail?sub?(objectClass=gluuPerson) - If you want to re-enable email uniqueness, uncomment the above line
- Restart the SOL Server with
service solserver restart