Local User Management#
In this document we cover managing people in the Gluu Server's LDAP Directory and graphical user interface "oxTrust".
We also briefly cover the Gluu Server's very basic out-of-the-box user registration feature. However, when it comes to user registration, we almost always recommend writing your own registration process, then using the SCIM 2.0 APIs to register the users in your Gluu service.
Manage data in Gluu LDAP#
All data generated by and stored in the Gluu Server is available in the local LDAP server included in every deployment. This includes OpenID Connect client data, session data, tokens, user data, and more.
Use an LDAP browser like JXplorer and find configuration data in /opt/gluu-server-3.1.6/etc/gluu/conf/ox-ldap.properties, e.g.:
bindDN: cn=directory manager
bindPassword: foobar
servers: localhost:1636
Since Gluu's LDAP port, 1636, is not exposed to the Internet, you need to establish a tunnel from your computer to the target Gluu Server's LDAP.
The below example shows how to connect to and access the internal LDAP server:
- Create a tunnel:
ssh -L 5901:localhost:1636 root@[ip_of_Gluu_server] - Open an LDAP browser
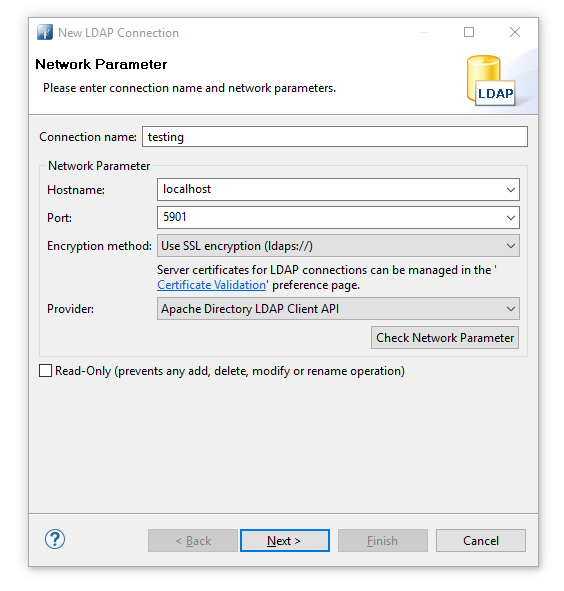
- Create a new connection
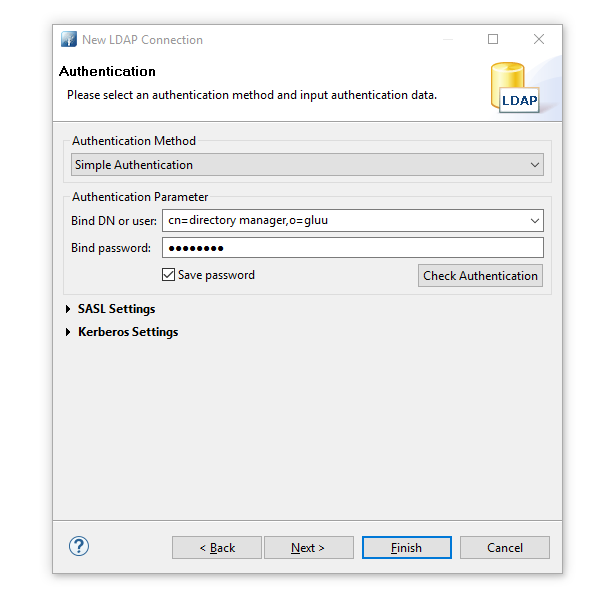
- Perform authentication. 'Password' is the the password of 'admin' user.
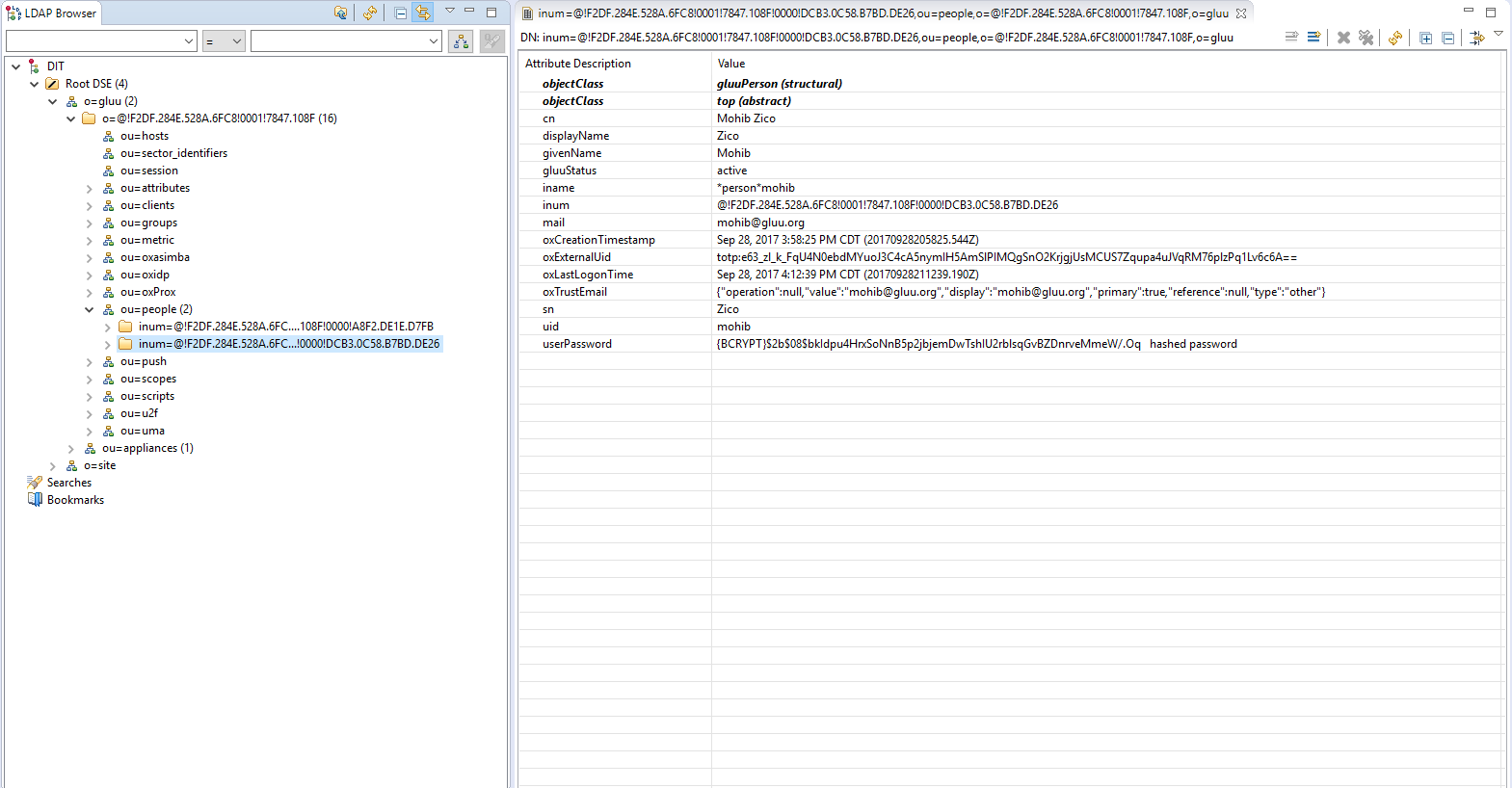
- Browse ldap and go to 'ou=people'.
Manage People in oxTrust#
Managing user data can also be performed in oxTrust, the server admin GUI. To manage people in oxTrust, navigate to User > Manage People.
From this interface you can add and search users. Because the user database can potentially be very large, a value with at least two characters is required in the search field. In other words, you can not click search with a blank entry to populate all users. If you need to see all users, this is best performed in the Gluu LDAP server, as described above.
Upon performing a user search in oxTrust, a list will be populated with all users that match the search.
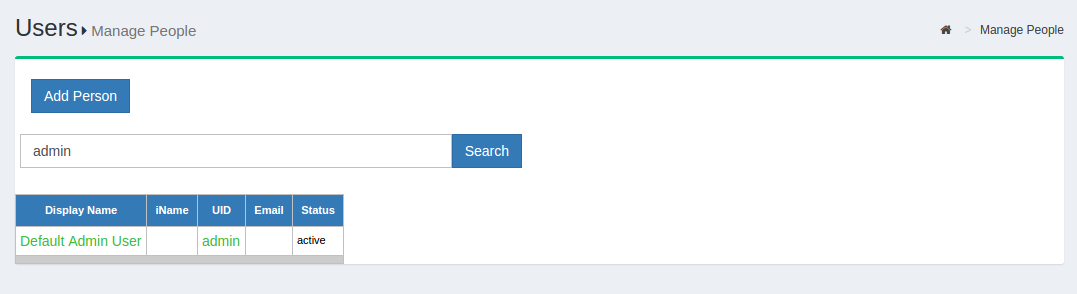
To edit a user, simply click on any of the hyperlinks associated with that user and you will be taken to a user management interface where you can modify specific attributes relating to that user.
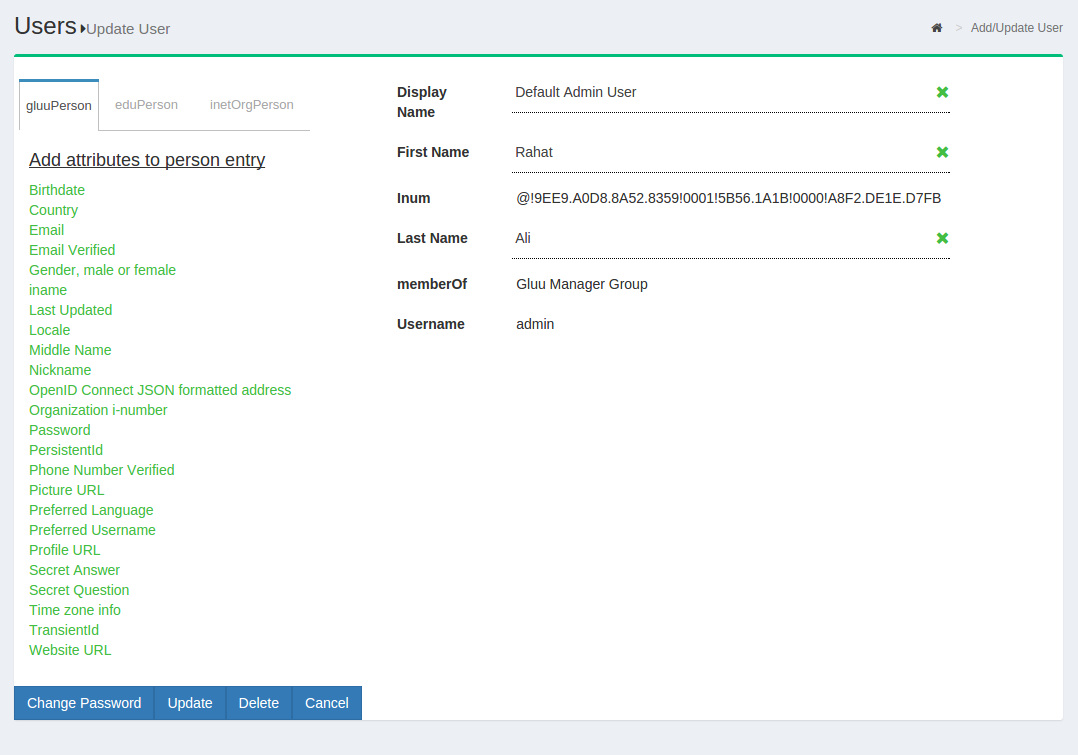
Managing associated Pairwise IDs#
If the user has any associated Pairwise IDs, they will be displayed in a table on the bottom of the page. If an associated Pairwise ID needs to be removed, just click the Remove button.
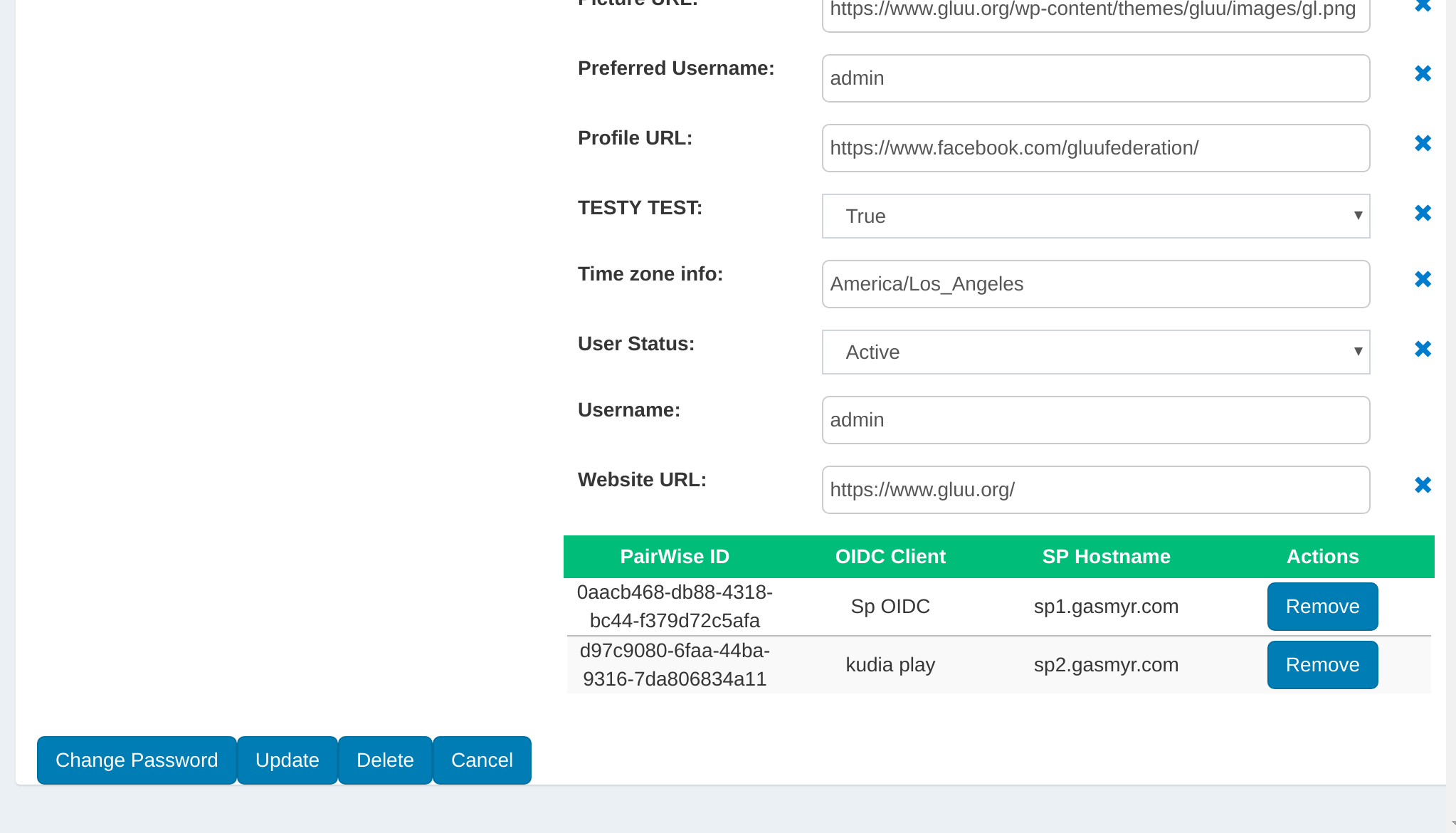
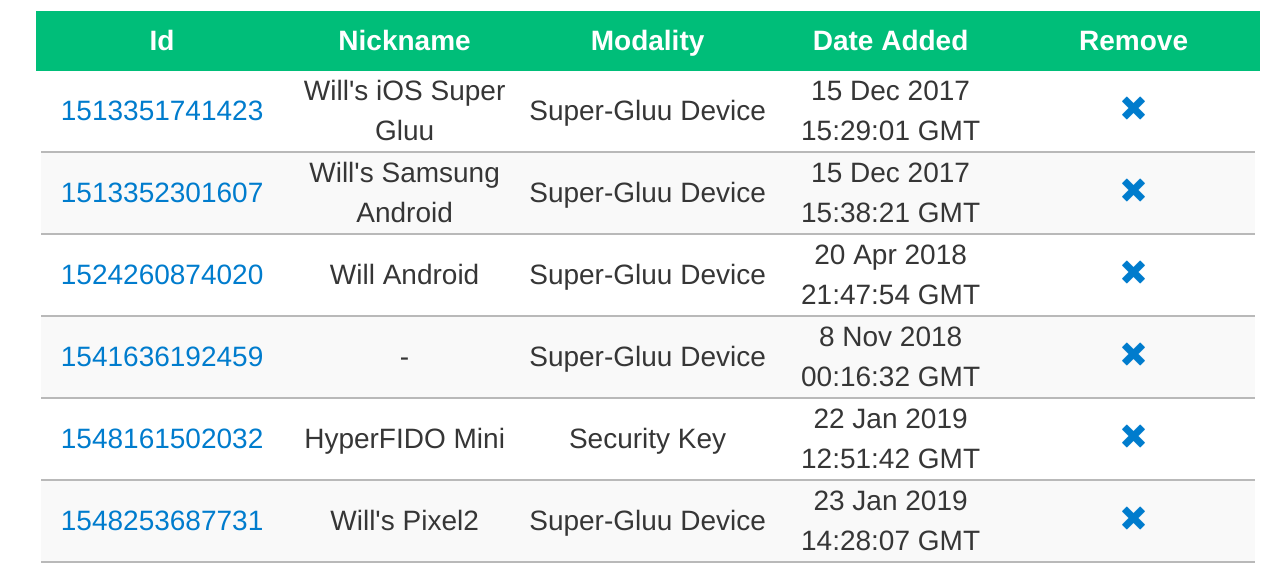
Managing associated 2FA devices#
Likewise, if the user has any associated 2FA devices, they will be displayed in their own table at the bottom of the page. If an associated 2FA device needs to be removed, just click the Remove button.
Managing associated authorizations#
If the user has previously granted authorization to release their data to specific applications, this can be managed in LDAP. There is a branch called ou=clientAuthorizations,inum=...,ou=people,o=...,o=gluu
There can be several oxId= ... entries underneath. Every entry has the oxAuthClientId attribute, which is the inum of the OpenID client for which the user has authorized consent.
To remove consent for a user/client pair, manually remove the corresponding oxId=... subentry.
To also remove the refresh tokens, check the clients branch ou=clients,o=...,o=gluu.
Under the oxAuthGrantId=... branch, there will be subentries for uniqueIdentifier=.... Those have the following attributes which map client, user and type of token issued: oxAuthClientId, oxAuthUserId, oxAuthTokenType. Delete the uniqueIdentifier=... entries as needed. oxAuth will also clear those automatically as per the oxAuthExpiration attribute.
Manage Groups in oxTrust#
Out of the box, the Gluu Server includes one group: the Gluu Manager Group (gluuManager). Groups can be added and populated as needed. By using the Manage Groups feature, the Gluu Server Administrator can add, delete or modify any group or user within a group. The list of available groups can be viewed by hitting the Search button with a blank search box.
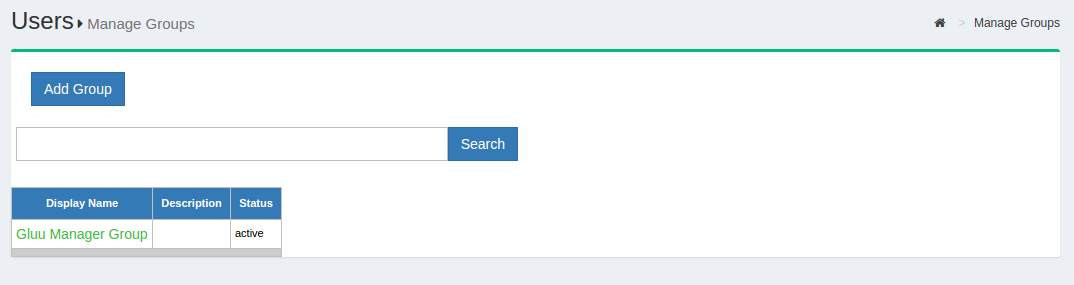
The Gluu Server Administrator can modify information such as Display Name, Group Owner, Visibility type etc. The Server Administrator can also add or delete users within existing groups. The group information is represented as shown below.
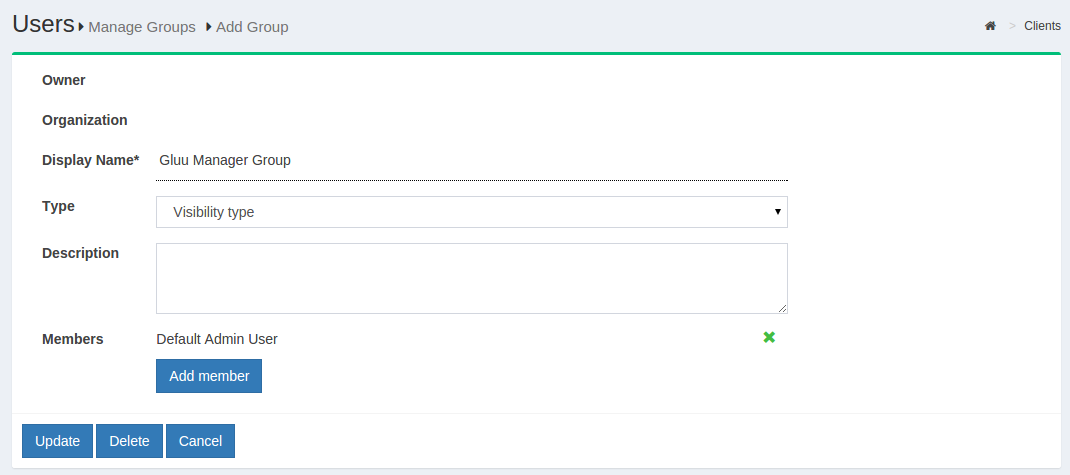
If any member of the Organization is required to be added in any specific group, this can be achieved be clicking on the Add Member button. The flow is Add Member --> Search the name/email of the user --> Select the user --> Click OK --> Update.
Import People in oxTrust#
Gluu administrators can import users from an excel file by navigating to Users > Import People.
-
Click the
Addbutton to select the file from which the users will be imported. The supported excel formats arexlsandxlsx. -
If one field should contain multiple values, provide them in the same cell separated by semicolons, as in column H in the following example:
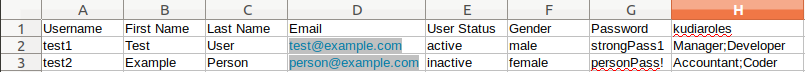
- Click the
Validatebutton to validate the user list.
- Click
Importto complete the import of users.
File structure#
The excel file needs to contain the following default fields from which user data will be pulled:
-
Username
-
First Name
-
Last Name
-
Email
Note
Make sure to use the exact spelling as shown above.
Gluu administrators can define additionals supported fields for import by navigating to:
-
Log into Gluu Admin UI
-
Navigate to
Organization Configuration>JSON Configuration -
Select
oxTrust Import Configurationtab
User Registration#
The Gluu Server includes a very basic user registration feature. Instructions for using Gluu's user registration functionality follows.
Note
In most situations, we recommend writing a custom registraton page that uses Gluu's SCIM 2.0 endpoints to send user identity data to Gluu. Using SCIM will give you more control and flexibility over the registration process. Also, since oxTrust is frequently not Internet facing, the registration page (https://<hostname>/identity/register) may not be available to a user on the web.
Enable User Registration#
To enable user registration via the Gluu Server, follow these steps:
- Navigate to
Custom Scriptsand select theUser Registrationtab; - Find the
Enabledfield and check the box; - Click the
Updatebutton at the bottom of the page; - New users will now be able to register for accounts at:
https://<hostname>/identity/register.
Note
When user registration is handled via oxTrust, users can not be added to a backend LDAP or Active Directory server. This means that self-registration via oxTrust is only effective if users are authenticated by GluuLDAP (and not a backend LDAP or AD server).
Adding attributes to registration#
A limited number of attributes are present in the default registration form. If more attributes are needed they can be added via the GUI by navigating to Organization Configuration > Manage Registration. Learn how to add attributes to the default registration form.
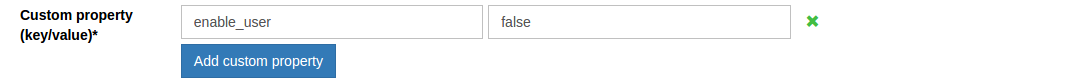
Manual approval of new users#
By default the Custom property (key/value) field will include the value: enable_user and true. This enables new users to login as soon as registration is complete. If you want to manually review and approve new user registrations, you can set this value to false as shown in the screenshot below.