OpenID Connect Stepped-up Authentication#
Overview#
This tutorial describes how to add OpenID Connect Authorization code flow stepped-up authentication by configuring the gluu-openid-connect plugin.
In the demo, the user will first authenticate with basic (auth_ldap_server) auth, then needs to pass one more OTP authentication step for the /payments/ resource.
It is fully configurable, you can add stepped-up authentication on multiple resources. Check here for more details.
Requirements#
-
Gluu Gateway 4.2.0: This is an OpenID Connect relying party(RP) between the client and the upstream service. Install Gluu Gateway. The oxd server is a static API web application that will install during GG installation.
-
Protected (Upstream) Website: In our demo, we are using a demo Node.js App, available here.
Gluu Server configuration (OpenID Connect Server)#
First, add OTP stepped-up authentication by enabling the OTP ACR in the OP Server. Configure the following settings inside your Gluu Server:
-
In oxTrust, navigate to
Configuration>Manage Custom Scripts -
Enable the
OTPscript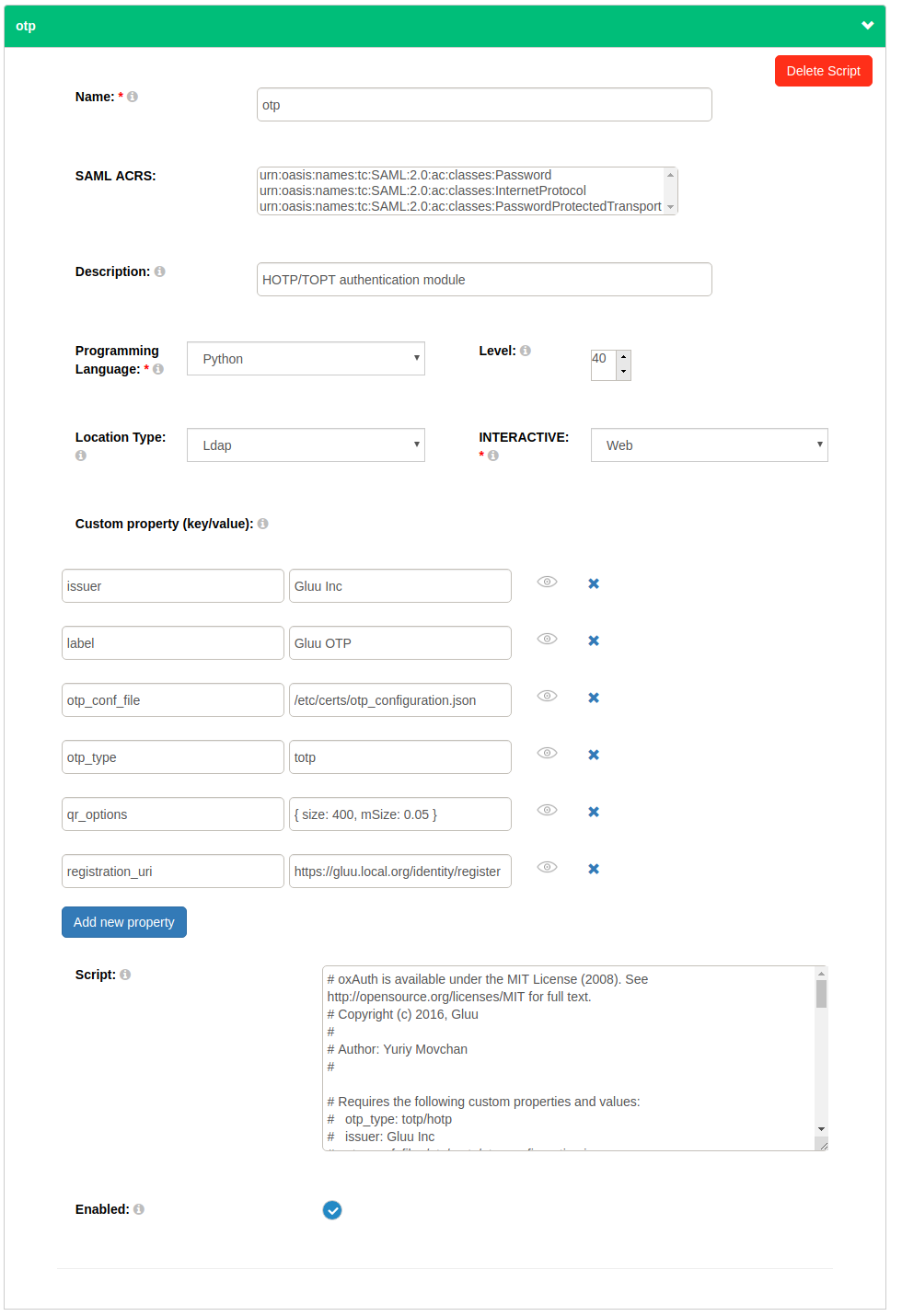
-
Now just confirm that it is enabled successfully by checking your OP discovery endpoint
<your_op_server>/.well-known/openid-configuration, it should showotpin theacr_values_supportedproperty.
Gluu Gateway configuration (RP)#
In this demo, we are going to register and protect the whole upstream service (the website) using gluu-openid-connect plugin. We will register the /payments/?? path with the OTP ACR and for all other resources, the default auth_ldap_server. As a result, a request for /payments will ask for an additional OTP authentication step to access the resource.
Note
The GG UI is only available on the localhost. Since it is on a remote machine, we need SSH port forwarding to reach the GG UI. Plugin configuration can be done either via REST calls or via the Gluu Gateway web interface.
Applications and their ports:
| Port | Description |
|---|---|
| 1338 | Gluu Gateway Admin GUI |
| 8001 | Kong Admin API |
| 8000 | Kong Proxy Endpoint |
| 443 | Kong SSL Proxy Endpoint. Kong by default provides port 8443 for SSL proxy, but during setup changes it to 443. |
| 8443 | oxd Server |
Log in to the Gluu Gateway Admin GUI(:1338) and follow the below steps.
Add Service#
Register the upstream website as a Service.
This demo uses http://localhost:4400 as the Upstream Website, the application where OpenID Connect Authentication is added. End-users always request to the Kong proxy first, then the plugin performs authentication. If it's successful, Kong will forward the request to the upstream website and serve the content returned by the upstream website.
Follow these step to add a Service using GG UI
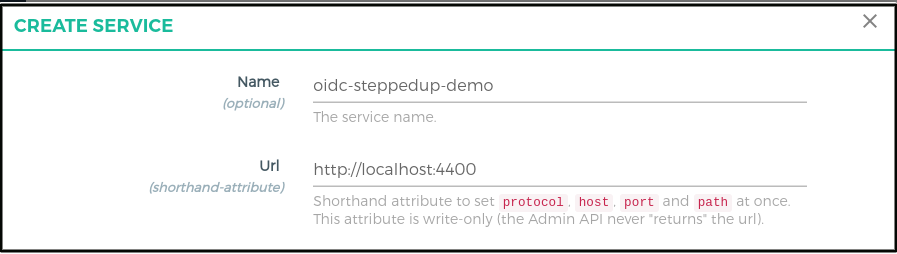
- Click
SERVICESon the left panel - Click on
+ ADD NEW SERVICEbutton - Fill in the following boxes:
- Name: oidc-steppedup-demo
- URL: http://localhost:4400
Add Route#
Follow these steps to add a route:
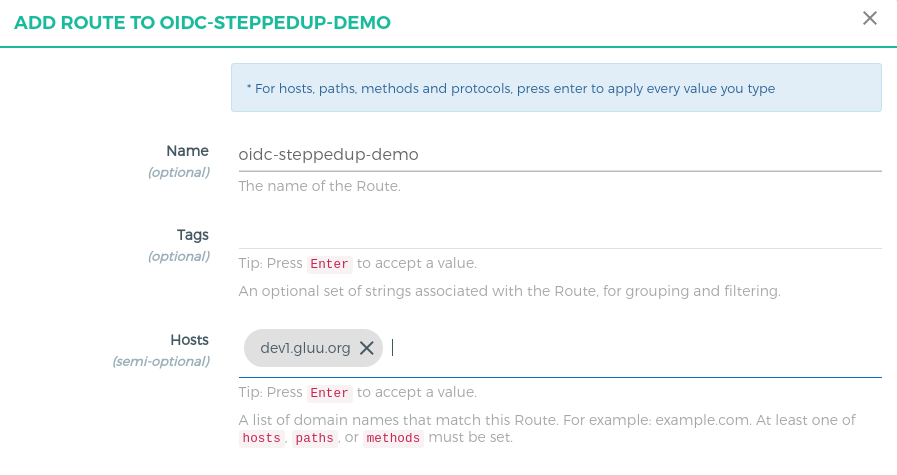
-
Click on the
oidc-steppedup-demoservice -
Click
Routes -
Click the
+ ADD ROUTEbutton -
Fill in the following boxes:
- Name: oidc-steppedup-demo
- Hosts:
<your-server-host>,Tip: Press Enter to accept value. This tutorial uses a server with an updated/etc/hostsfile. This is the host that will be requested in the browser after configuration. If using live servers, register the domain host instead. The rest of the tutorial will usedev1.gluu.orgas an example, replace it with your host. Check the Kong docs for more routing capabilities.
Configure Plugin#
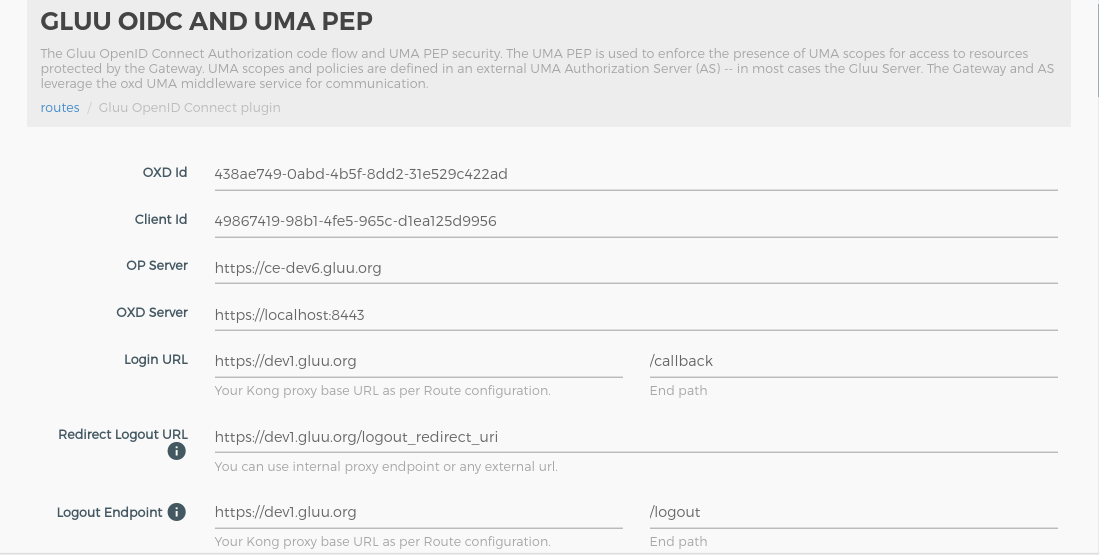
- Click
ROUTESon the left panel - Click on the
route id/namewithdev1.gluu.orgas the host - Click on
Plugins - Click on
+ ADD PLUGINbutton - You will see
Gluu OIDC & UMA PEPtitle and+icon in pop-up. - Click on the
+icon and it will show the below form. Add the ACR expression as in the below screenshots.OTPstepped-up auth for path/payments/??auth_ldap_serverauthentication for all other paths. Check here for more details about ACR expressions.
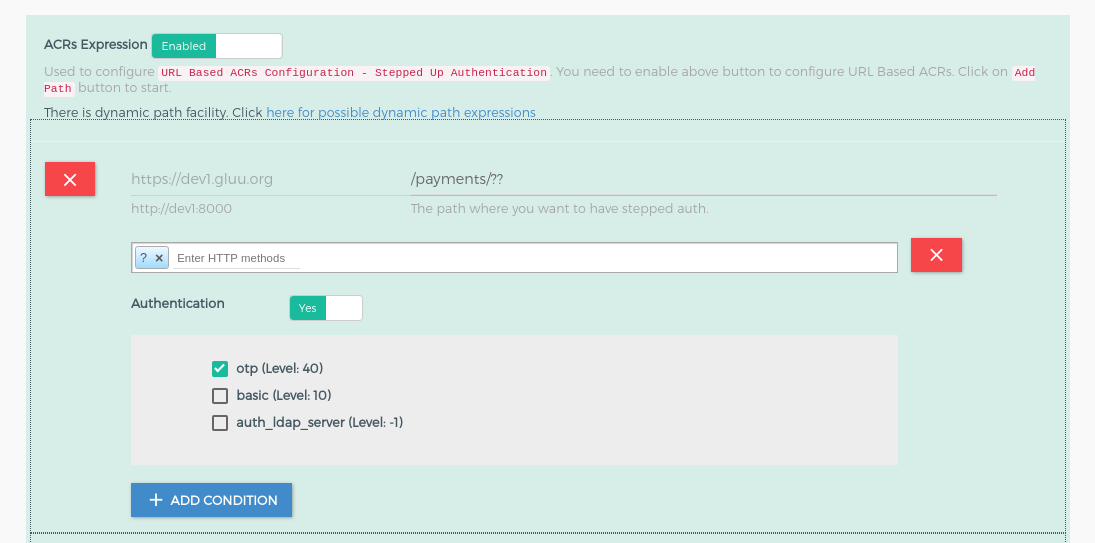
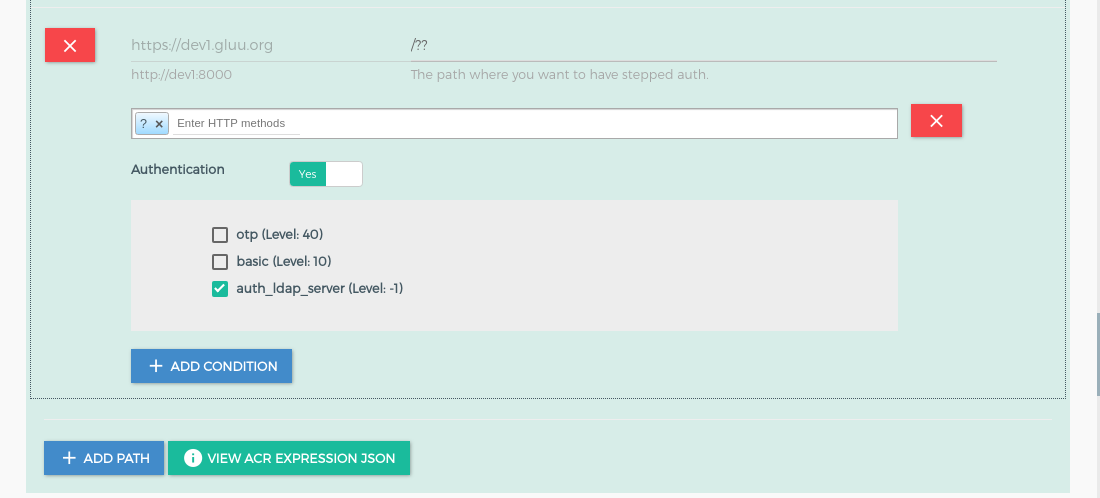
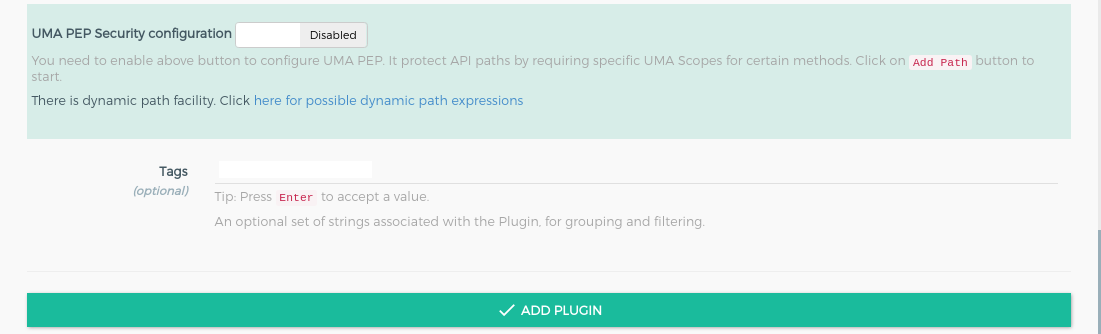
This completes configuration. Next, request the Kong proxy at https://<your_host> in the browser. In this example, the host is https://dev1.gluu.org.
Authentication#
-
Once you send a request to the Kong proxy, the plugin will redirect the request to the OP side. The OP will request for the
usernameandpassword, because we added theauth_ldap_serverACR for any path/??.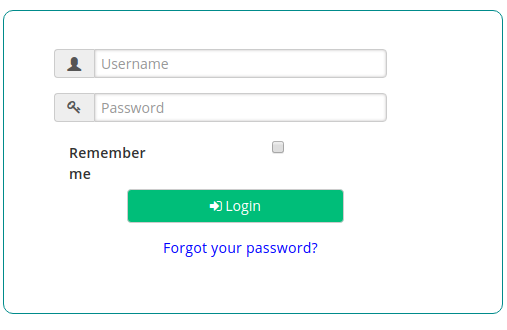
After successful authentication, the OP will display all requested permissions. Click
Allow.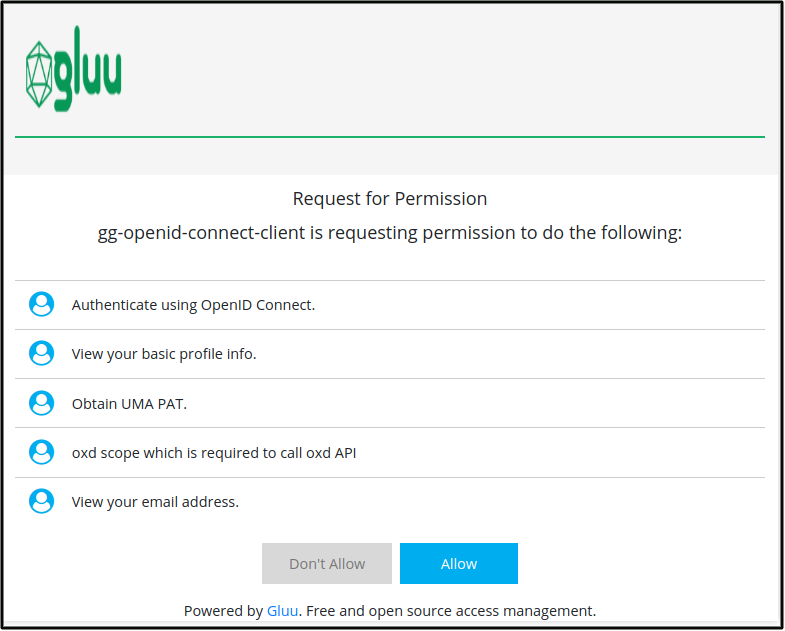
-
After clicking
allow, you will get back to the Kong proxy and the plugin will serve the default home page of the upstream service.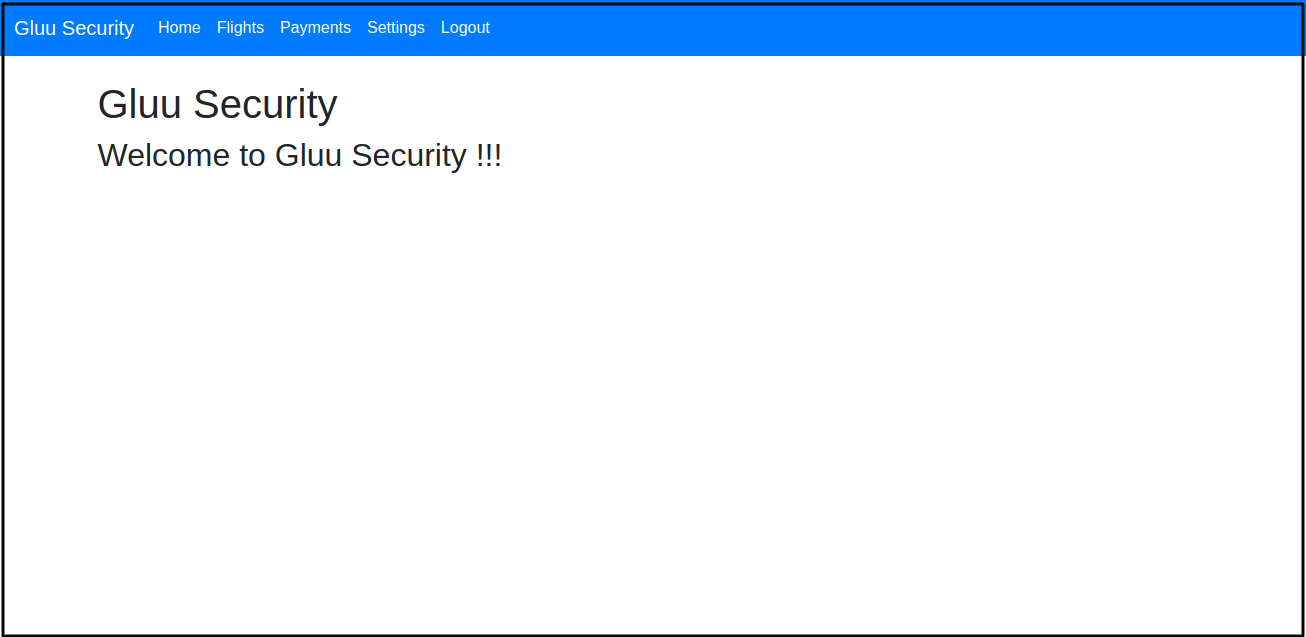
Click on
Flights. It is also in the/??path, so the user already has permission to access this resource.
-
Now click
Payments, on which we added theOTPstepped-up authentication. The plugin will redirect again to the OP. As per theOTPscript, it will ask for theusernameandpassword.
After successful authentication, the OP Server asks you to enroll in a device. Scan the displayed QR Code in an authenticator application, then click on
Finish. Check the Gluu CE docs for supported OTP applications.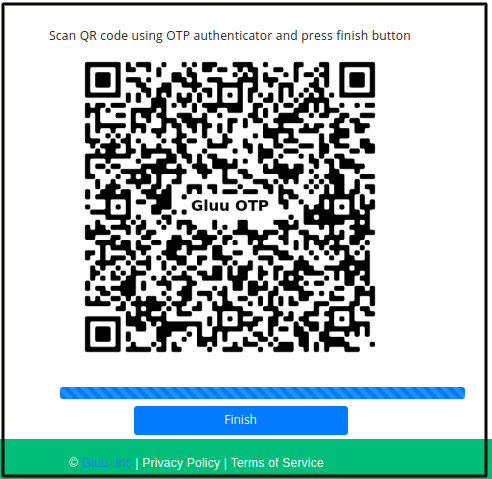
After successful enrollment, it will prompt to enter the OTP. Enter the OTP from the authenticator application and click on
Login.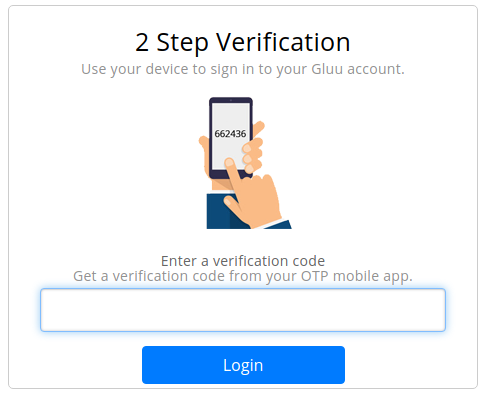
-
After
OTPauthentication, the OP server will redirect back to the Kong proxy and serve thePaymentspage.
For more details and configuration, check the gluu-openid-connect plugin docs.